The Role of Blockchain in Ensuring Digital Privacy is exploding onto the scene, shaking up how we think about data security. Forget Big Brother – blockchain’s decentralized nature throws a wrench into the traditional, centralized systems that leave our personal info vulnerable. We’re talking about a game-changer, a technology that could redefine privacy in the digital age. This deep dive explores how blockchain’s unique architecture, encryption methods, and focus on user control are revolutionizing data protection.
From cryptographic hashing to the nuances of permissioned versus permissionless blockchains, we’ll unpack the technical aspects in a way that’s both informative and engaging. We’ll explore real-world applications, examine the challenges, and even peek into the future of blockchain’s role in securing our digital lives. Get ready to understand why this tech is more than just hype; it’s a potential lifeline for digital privacy in a world increasingly obsessed with our data.
Decentralization and Privacy: The Role Of Blockchain In Ensuring Digital Privacy
In today’s digital landscape, where data breaches are commonplace and centralized entities hold immense power over our personal information, blockchain technology emerges as a beacon of hope for enhanced digital privacy. Its decentralized architecture fundamentally alters the power dynamic, offering a robust alternative to traditional, centralized systems.
Blockchain’s decentralized nature significantly enhances digital privacy by distributing data across a network of computers instead of storing it in a single, vulnerable location. This inherent distribution makes it exponentially harder for malicious actors to access and compromise user data. Imagine a single, gigantic database containing everyone’s personal information – a hacker’s dream. Now imagine that same information spread across thousands of independent computers, each holding only a small fraction of the whole. The task of accessing all that data becomes a herculean, practically impossible feat.
Eliminating Single Points of Failure, The Role of Blockchain in Ensuring Digital Privacy
Centralized systems, like those used by many social media platforms or online retailers, are vulnerable because they possess a single point of failure: the central server. If this server is compromised, all the data it holds is at risk. Blockchain eliminates this single point of failure. The distributed ledger technology ensures that even if some nodes in the network are compromised, the integrity of the data remains intact, thanks to the redundancy built into the system. For example, if a hacker gains access to one node in a Bitcoin network, they won’t have access to the entire blockchain, only a small part of it. The rest of the network continues to operate normally, safeguarding the overall data integrity.
Privacy Implications of Permissioned and Permissionless Blockchains
Permissioned and permissionless blockchains differ significantly in their privacy implications. Permissionless blockchains, like Bitcoin, are open to anyone, offering a high degree of anonymity but potentially less control over data access. Permissioned blockchains, on the other hand, require authorization to participate, allowing for greater control over who can access and modify data. This makes them suitable for scenarios requiring higher levels of privacy and data security within a specific community or organization. For instance, a supply chain using a permissioned blockchain could track goods securely while maintaining confidentiality among its authorized participants. Conversely, the public nature of a permissionless blockchain might not be ideal for sensitive personal data.
Blockchain Mechanisms for Data Protection
Blockchain technology employs several mechanisms to protect user data from unauthorized access. Cryptographic hashing ensures data integrity, making any unauthorized alteration immediately detectable. Cryptographic keys and digital signatures provide authentication and authorization, verifying the identity of users and preventing unauthorized access. Furthermore, the immutability of the blockchain prevents data tampering and deletion, creating a permanent and trustworthy record of transactions and data. The combination of these mechanisms offers a significant layer of protection against various threats, unlike centralized systems that rely on single security measures that are easily breached.
Data Encryption and Security
Blockchain technology, at its core, is designed to enhance security and privacy. This is achieved through a combination of sophisticated cryptographic techniques and decentralized architecture. Understanding how these elements interact is crucial to grasping blockchain’s potential in safeguarding sensitive information.
Several encryption methods are employed to protect data within a blockchain system. These methods vary in complexity and application, often working in tandem to provide robust security. The choice of encryption technique depends heavily on the specific needs of the blockchain and the sensitivity of the data being handled.
Symmetric Encryption
Symmetric encryption utilizes a single key for both encryption and decryption. This approach is generally faster than asymmetric encryption but requires secure key exchange between parties. Examples include AES (Advanced Encryption Standard) and DES (Data Encryption Standard), commonly used to encrypt data stored on the blockchain or transmitted between nodes. AES, in particular, is widely considered a strong and reliable encryption algorithm. The security of symmetric encryption hinges entirely on the secrecy of the key; if compromised, the encrypted data becomes vulnerable.
Asymmetric Encryption
Unlike symmetric encryption, asymmetric encryption employs two keys: a public key for encryption and a private key for decryption. This allows for secure communication without the need for pre-shared secrets. RSA (Rivest-Shamir-Adleman) and ECC (Elliptic Curve Cryptography) are prominent examples. Public keys can be freely distributed, while private keys must remain confidential. This method is vital for digital signatures and verifying the authenticity of transactions on the blockchain. Imagine a scenario where Alice wants to send Bob a secure message. Alice uses Bob’s public key to encrypt the message. Only Bob, possessing the corresponding private key, can decrypt it.
Cryptographic Hashing and Data Integrity
Cryptographic hashing plays a pivotal role in ensuring data integrity and privacy within blockchain systems. Hash functions are one-way algorithms that transform any input data into a fixed-size string of characters (the hash). Even a tiny change in the input data results in a drastically different hash. This property is fundamental to blockchain’s security, as any tampering with the data would be immediately detectable by comparing the hash of the modified data with the original hash stored on the blockchain. SHA-256 and SHA-3 are examples of widely used hash functions. For example, if a transaction record is altered, the resulting hash will differ from the one recorded on the blockchain, immediately revealing the manipulation.
Consensus Mechanisms and Privacy
Different consensus mechanisms affect the privacy aspects of a blockchain. Proof-of-Work (PoW) systems, while robust in terms of security, often lack strong privacy features because transaction details are publicly visible. Proof-of-Stake (PoS) mechanisms, on the other hand, can offer some degree of enhanced privacy depending on their specific implementation. For instance, some PoS systems use techniques like sharding to improve scalability and, potentially, privacy by reducing the amount of data each node needs to process and store. However, even in PoS systems, transaction information may still be partially accessible, depending on the level of transparency designed into the system.
A Hypothetical Privacy-Focused Blockchain
Consider a hypothetical blockchain designed with a strong emphasis on data encryption and user anonymity. This system would leverage ring signatures, a cryptographic technique that allows a group of users to sign a transaction without revealing which specific user within the group signed it. The blockchain would use a consensus mechanism like a modified version of Proof-of-Stake, where validator selection is randomized and opaque to enhance anonymity. Data encryption would be implemented using a combination of symmetric and asymmetric encryption, with AES used for encrypting transaction data and ECC used for digital signatures. The system would employ zero-knowledge proofs to allow users to prove certain facts about their transactions without revealing sensitive details. Furthermore, a robust key management system would be critical to ensure the security of private keys and prevent unauthorized access. This system would aim for a balance between security, privacy, and efficiency, making it suitable for applications demanding a high level of confidentiality.
Pseudonymity and Anonymity
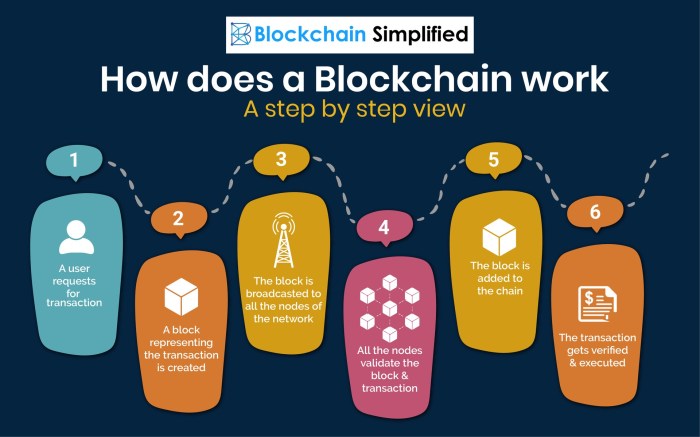
Source: blockchainsimplified.com
Blockchain technology, at its core, offers a fascinating dance between transparency and privacy. While all transactions are recorded on a public ledger, the identity of the participants doesn’t always need to be fully revealed. This is where pseudonymity and anonymity come into play, offering different levels of privacy protection within the blockchain ecosystem. Understanding the nuances of each is crucial for navigating the complexities of this digital landscape.
Pseudonymity, in the blockchain context, refers to using an alias or a pseudonym instead of your real-world identity. Think of it like using a pen name for your online writings – everyone can see your work, but they don’t necessarily know who you are. Anonymity, on the other hand, goes a step further, aiming to completely conceal your identity from all observers. It’s like wearing a mask in a crowd – no one can identify you.
Blockchain’s decentralized nature offers a potential solution to the privacy concerns surrounding data collection, especially pertinent given the increasing use of voice assistants. The rise of always-listening devices raises serious questions about data security, as explored in this insightful article, The Rise of Voice Assistants: What’s Next for AI-Powered Devices? , highlighting the need for robust privacy safeguards.
Ultimately, blockchain could be a key player in building a more private future for AI-powered technologies.
Benefits and Drawbacks of Pseudonymous Identities on Blockchain Networks
Pseudonymous identities offer a compelling middle ground. They allow for participation in decentralized systems while still offering a degree of privacy. The benefits include increased security against doxing and identity theft, fostering greater freedom of expression and participation in online communities, and facilitating secure transactions without revealing sensitive personal information. However, drawbacks exist. Pseudonymity can be exploited for illicit activities, making it challenging to track malicious actors. It also presents difficulties in resolving disputes or verifying identities when necessary, potentially hindering the adoption of blockchain in regulated sectors.
Comparison of Anonymity Levels Across Different Blockchain Platforms
Different blockchain platforms offer varying degrees of anonymity. Public blockchains like Bitcoin, while pseudonymous, leave a trail of transactions linked to public addresses. This trail, while not directly revealing personal identities, can be analyzed to infer connections and potentially de-anonymize users through techniques like transaction graph analysis. Privacy-focused blockchains like Zcash and Monero, however, employ advanced cryptographic techniques like zero-knowledge proofs to mask transaction details, offering significantly higher levels of anonymity. Each platform makes trade-offs between privacy and scalability or transaction speed.
Examples of Blockchain Applications Prioritizing User Anonymity
Several blockchain applications prioritize user anonymity to protect sensitive information and enable secure interactions. For instance, Monero is often used for private cryptocurrency transactions, ensuring sender and receiver identities remain hidden. Other applications explore anonymous voting systems on blockchain, allowing individuals to cast votes without revealing their choices. Decentralized identity solutions also leverage blockchain to manage digital identities while offering enhanced privacy controls.
Comparison of Blockchain Anonymity Solutions
The following table compares several prominent blockchain anonymity solutions, highlighting their strengths, weaknesses, and typical use cases.
| Solution | Strengths | Weaknesses | Use Cases |
|---|---|---|---|
| Bitcoin | Relatively mature and widely adopted; transparent and auditable | Pseudonymous, not anonymous; transaction history can be analyzed | Cryptocurrency transactions, digital asset management |
| Zcash | Offers shielded transactions for enhanced privacy | More complex to use than Bitcoin; scalability challenges | Private cryptocurrency transactions, confidential payments |
| Monero | Strong anonymity features; ring signatures and stealth addresses | Relatively newer technology; can be less efficient than other blockchains | Private cryptocurrency transactions, anonymous donations |
| Ethereum (with privacy-enhancing protocols) | Flexible and programmable; allows for integration with privacy tools | Privacy features are often add-ons, not native; can be complex to implement | Decentralized applications with privacy requirements |
Data Ownership and Control
Source: nix-united.com
Blockchain technology fundamentally shifts the paradigm of data ownership, putting the power back in the hands of the user. Unlike traditional centralized systems where corporations or governments hold and control your data, blockchain allows for decentralized data management, granting individuals greater autonomy and transparency over their personal information. This empowerment extends to various aspects, from data portability and interoperability to enhanced governance and compliance.
Blockchain facilitates data ownership by creating a verifiable and immutable record of data transactions. Each piece of data is represented as a cryptographic hash, linked to previous and subsequent transactions, forming a secure and transparent chain. This ensures that data cannot be altered or deleted without detection, providing users with a high degree of confidence in the integrity of their information. This level of control is particularly relevant in sensitive areas like healthcare, finance, and identity management.
Data Portability and Interoperability
Blockchain’s decentralized nature simplifies data portability. Imagine switching healthcare providers – with blockchain, your medical records could be easily transferred securely and verifiably, without relying on intermediaries. Interoperability, the ability of different systems to seamlessly exchange data, is also enhanced. Various applications can access and utilize your data, provided you grant permission, without the need for complex data migration processes. For example, a blockchain-based identity system could allow you to share your verified identity with different services, eliminating the need to repeatedly provide the same information. This fosters a more efficient and user-friendly digital ecosystem.
Blockchain’s Implications for Data Governance and Compliance
Blockchain enhances data governance by providing a clear audit trail of data access and usage. This increased transparency helps organizations comply with regulations like GDPR and CCPA, which emphasize user consent and data control. Furthermore, smart contracts, self-executing contracts with the terms of the agreement directly written into code, can automate data governance processes, ensuring compliance and reducing the risk of human error. For example, a smart contract could automatically delete user data upon request, guaranteeing adherence to data deletion policies.
Managing and Controlling Data on a Blockchain Platform
Managing your data on a blockchain platform involves several steps. First, you need to choose a reputable blockchain platform or application that aligns with your needs and values. This often involves researching the platform’s security measures, privacy policies, and user reviews. Next, you’ll create a digital identity or wallet on the platform, which will act as your access point to your data. This typically involves creating a secure password and potentially linking a secondary authentication method, like two-factor authentication. Once your identity is established, you can then upload or store your data on the blockchain, utilizing the platform’s tools and functionalities to manage access permissions and data sharing. Regularly reviewing your data, access permissions, and transaction history is crucial to maintaining control over your information. You should also stay informed about platform updates and security patches to ensure the ongoing protection of your data.
Blockchain’s Role in Data Governance
Blockchain technology, with its inherent transparency and immutability, offers a revolutionary approach to data governance. It presents a powerful tool for establishing trust and accountability in the management and control of sensitive information, moving beyond traditional, often opaque, systems. This shift promises to empower individuals and organizations alike with greater control over their data destiny.
By leveraging blockchain’s decentralized and secure nature, organizations can build robust and auditable data governance frameworks. This allows for greater transparency in data handling processes, fostering trust among stakeholders and facilitating compliance with evolving data privacy regulations.
Smart Contracts for Enforcing Data Privacy Policies
Smart contracts, self-executing contracts with the terms of the agreement directly written into code, are a crucial component of blockchain-based data governance. These contracts can automatically enforce data privacy policies and regulations, ensuring compliance without the need for intermediaries. For example, a smart contract could be programmed to automatically delete user data after a specified period, or to restrict access to sensitive information based on pre-defined criteria. This automation not only improves efficiency but also minimizes the risk of human error or intentional breaches of privacy. The code itself becomes the enforcer of the agreed-upon rules, offering a level of accountability that’s difficult to achieve with traditional methods.
Challenges and Opportunities in Blockchain Data Governance
Implementing blockchain for data governance isn’t without its hurdles. Scalability remains a significant challenge, especially when dealing with large volumes of data. The complexity of integrating blockchain technology with existing systems can also be daunting, requiring substantial investment in infrastructure and expertise. Furthermore, the legal and regulatory landscape surrounding blockchain is still evolving, creating uncertainty for organizations looking to adopt this technology.
However, the potential benefits outweigh these challenges. Blockchain’s ability to enhance data transparency and accountability could lead to greater trust in data-driven decision-making. This, in turn, could unlock new opportunities for innovation and collaboration, particularly in sectors with strict data privacy requirements, such as healthcare and finance. The ability to track data usage and provenance with unparalleled precision opens the door to new levels of data security and compliance.
Illustrative Scenario: Enhancing Data Transparency and Accountability
Imagine a healthcare system utilizing a blockchain-based data governance platform. Patient data, encrypted and stored on the blockchain, is accessible only to authorized personnel. Each access attempt, along with the user’s identity and the specific data accessed, is recorded immutably on the blockchain. This creates a complete and auditable trail of data usage. A visual representation would show a network of interconnected nodes (representing healthcare providers, patients, and regulatory bodies) connected to a central blockchain. Each data access event is represented as a block added to the chain, displaying timestamps, user IDs, and data access details. This creates a visually clear and readily verifiable record of all data interactions, making it easy to track data usage and identify any unauthorized access attempts. This detailed audit trail empowers both patients and regulatory bodies to oversee the management of sensitive health information, significantly improving accountability and trust.
Case Studies and Real-World Applications
Blockchain’s potential for enhancing digital privacy isn’t just theoretical; it’s being actively explored and implemented across various sectors. Several successful projects demonstrate the technology’s ability to protect sensitive data while facilitating its secure exchange. However, challenges remain in scaling these solutions and addressing the complexities of real-world applications.
Healthcare Data Management
The healthcare industry is a prime candidate for blockchain’s privacy-enhancing capabilities. Imagine a system where patient medical records are securely stored on a decentralized blockchain, accessible only with the patient’s explicit consent. This eliminates the risk of data breaches and unauthorized access. One example is the use of blockchain to manage patient consent for data sharing, ensuring individuals retain control over their medical information. This allows healthcare providers to access only the necessary data while maintaining complete patient privacy. However, challenges include integrating blockchain with existing legacy systems and ensuring interoperability between different healthcare providers’ blockchain networks. The complexity of regulatory compliance and the need for robust data governance frameworks also present significant hurdles.
Financial Transactions and Identity Management
Blockchain’s impact on finance extends beyond cryptocurrencies. Its decentralized nature can bolster financial privacy by enabling secure and transparent transactions without revealing the identities of participants. Several projects utilize blockchain for secure identity management, allowing individuals to control their digital identities and selectively share information with trusted parties. For instance, some platforms use blockchain to verify identities without storing personally identifiable information centrally, mitigating the risk of large-scale identity theft. Despite the potential, scalability remains a challenge, especially when dealing with large volumes of transactions. The technical complexity of implementing blockchain solutions in established financial institutions and the need for robust regulatory frameworks also pose significant obstacles.
Supply Chain Transparency and Traceability
Blockchain technology can enhance privacy in supply chains by providing a secure and transparent record of product movement and origin. This allows consumers to verify the authenticity of products and track their journey from origin to consumer, while simultaneously protecting the sensitive data of involved parties. For example, a pharmaceutical company could use blockchain to track its drugs, ensuring their authenticity and preventing counterfeiting without revealing sensitive manufacturing details or compromising the privacy of individual suppliers. However, challenges include the need for widespread adoption across the supply chain and the potential for data manipulation if not properly secured.
Future Applications of Blockchain for Enhanced Digital Privacy
The potential applications of blockchain for enhanced digital privacy are vast and rapidly evolving. A robust and secure infrastructure is crucial for successful implementation.
- Decentralized Social Media Platforms: Blockchain can empower users with greater control over their data and interactions, reducing reliance on centralized platforms that often compromise privacy.
- Secure Voting Systems: Blockchain’s immutability and transparency can help build more secure and auditable voting systems, protecting voter privacy and preventing fraud.
- Data Marketplaces: Blockchain can facilitate the creation of data marketplaces where individuals can securely sell their data while maintaining control and receiving fair compensation.
- Enhanced Data Security for IoT Devices: Blockchain can provide a secure and decentralized framework for managing data generated by the growing number of Internet of Things (IoT) devices.
Last Point

Source: theruleinfinity.com
Ultimately, blockchain’s potential to revolutionize digital privacy is undeniable. While challenges remain, the technology’s inherent decentralization, robust encryption, and focus on user control offer a compelling path toward a more secure and private digital future. The journey from theoretical concept to widespread adoption is ongoing, but the implications for individuals and organizations alike are significant. The future of digital privacy may well be written on the blockchain.
