The Role of Blockchain in Digital Identity Management is shaking things up. Forget clunky, centralized systems vulnerable to hacks and breaches – blockchain offers a decentralized, secure, and transparent alternative. Imagine a world where you control your own digital identity, proving who you are without handing over sensitive data to corporations. That’s the promise of blockchain-based identity, and it’s a game-changer.
This revolution hinges on decentralized identifiers (DIDs) and verifiable credentials (VCs), giving individuals ultimate control over their personal information. We’ll dive deep into the tech, exploring how blockchain’s inherent security and immutability address the major weaknesses of traditional systems. From healthcare to finance, we’ll examine real-world applications already transforming how we verify identity, and discuss the hurdles – like scalability and standardization – that need to be overcome to fully unlock its potential.
Introduction to Digital Identity and its Challenges
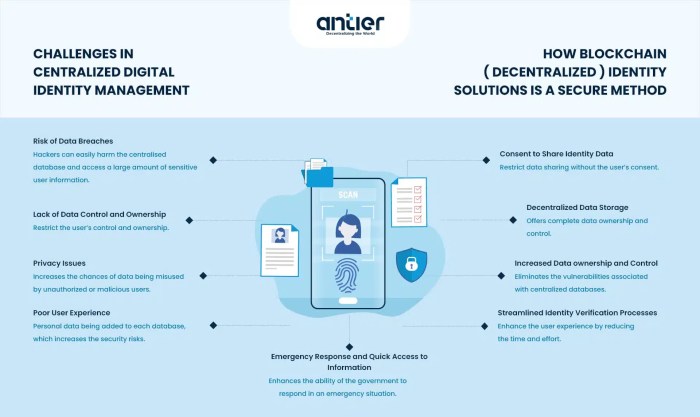
In today’s hyper-connected world, digital identity is no longer a futuristic concept; it’s the cornerstone of our online lives. From accessing online banking to verifying our identities for government services, we rely on digital systems to manage our personal information. However, the current landscape of digital identity management is riddled with vulnerabilities, raising serious concerns about security and privacy. The limitations of existing systems are increasingly apparent, highlighting the urgent need for innovative solutions.
The reliance on centralized systems is a major weakness. Traditional identity management often involves a single entity controlling vast amounts of personal data. This creates a single point of failure, making the system vulnerable to large-scale breaches and data leaks. Imagine a scenario where a major social media platform suffers a massive data breach – millions of users’ personal details, including names, addresses, and even financial information, are exposed. This isn’t a hypothetical situation; it’s a reality we’ve seen repeatedly. The consequences can range from identity theft and financial fraud to reputational damage and erosion of public trust.
Limitations of Centralized Identity Systems
Centralized systems, while seemingly convenient, are inherently fragile. Their susceptibility to hacking and data breaches poses significant risks. Furthermore, these systems often lack transparency, making it difficult for users to understand how their data is being collected, used, and protected. The lack of user control over personal data is another critical issue. Individuals often have limited options to correct inaccuracies or request the deletion of their information. This lack of control contributes to a sense of vulnerability and powerlessness. Moreover, these systems often struggle to adapt to the evolving needs of users and the digital landscape, making them inflexible and slow to respond to emerging threats. For instance, a centralized system designed for simple logins may struggle to handle the complexities of managing multiple identities across different platforms and services.
Real-World Examples of System Failures
The Equifax data breach of 2017 is a prime example of the devastating consequences of centralized system failures. The breach exposed the personal information of nearly 150 million people, including Social Security numbers, birth dates, and addresses. This led to widespread identity theft, financial losses, and significant reputational damage for Equifax. Similarly, numerous instances of data breaches at healthcare providers have exposed sensitive medical records, highlighting the vulnerabilities of centralized systems in handling sensitive personal data. The Cambridge Analytica scandal, while not strictly a data breach in the traditional sense, exposed the vulnerabilities of centralized data collection and the potential for misuse of personal information for political manipulation. These incidents underscore the need for more robust and secure methods of managing digital identities.
Blockchain Technology Fundamentals for Identity Management
Blockchain technology, with its revolutionary approach to data management, offers a compelling solution to the persistent challenges of digital identity. Its core principles directly address the vulnerabilities and inefficiencies inherent in traditional identity systems, paving the way for a more secure and user-centric digital identity landscape. This section delves into the fundamental aspects of blockchain that make it particularly well-suited for identity management.
At its heart, blockchain is a distributed, immutable ledger. This means that instead of a single entity controlling all identity data, the information is shared across a network of computers. Each transaction, or change in identity data, is recorded as a “block” and added to a chronologically ordered “chain.” This distributed nature makes it incredibly difficult to tamper with the data, a key advantage over centralized systems prone to single points of failure and data breaches.
Core Principles of Blockchain for Identity Management
Three key principles underpin blockchain’s efficacy in digital identity: decentralization, immutability, and cryptographic security. Decentralization distributes the responsibility for data management, reducing the risk of single points of failure and censorship. Immutability ensures that once data is recorded, it cannot be altered or deleted, maintaining the integrity and trustworthiness of identity information. Cryptographic security employs sophisticated encryption techniques to protect data from unauthorized access and modification. These principles work in concert to create a robust and reliable system for managing digital identities.
Secure digital identity, powered by blockchain, is changing the game. Imagine personalized AR experiences, like the ones explored in this awesome article on how augmented reality is enhancing the entertainment industry: How Augmented Reality is Enhancing the Entertainment Industry. This seamless integration of verified identities opens doors to personalized content and safer online interactions, solidifying blockchain’s role in the future of digital life.
Decentralization and Immutability Address Identity Management Challenges
Traditional identity systems often suffer from centralization, making them vulnerable to hacking and data breaches. A single point of failure, like a compromised database, can expose millions of identities. Blockchain’s decentralized architecture mitigates this risk. Data is not stored in one place but spread across a network, making it exponentially harder to compromise. Similarly, immutability addresses the issue of data manipulation. Once an identity record is verified and added to the blockchain, it cannot be altered without detection, ensuring the authenticity and integrity of the information. This addresses concerns about data falsification and identity theft, creating a more trustworthy system.
Comparison of Blockchain Architectures for Identity Management
Different blockchain architectures offer varying levels of decentralization, immutability, and scalability, impacting their suitability for identity management. The choice of architecture depends on the specific needs and priorities of the system. Consider the trade-offs between security, performance, and cost when selecting an appropriate blockchain architecture.
| Blockchain Type | Decentralization Level | Immutability Features | Scalability |
|---|---|---|---|
| Public Permissionless Blockchain (e.g., Bitcoin, Ethereum) | High | Very High – all transactions are cryptographically secured and auditable by all participants. | Relatively Low – transaction speeds can be slow and fees can be high. |
| Private Permissioned Blockchain (e.g., Hyperledger Fabric, R3 Corda) | Moderate to High (depending on the level of permissioning) | High – transactions are cryptographically secured and auditable within the permissioned network. | Moderate to High – offers better scalability than public blockchains due to controlled access. |
| Consortium Blockchain (e.g., Hyperledger Besu) | Moderate | High – transactions are cryptographically secured and auditable within the consortium network. | Moderate – offers a balance between decentralization and scalability. |
| Hybrid Blockchain | Variable – combines features of public and private blockchains. | Variable – depends on the design and implementation of the hybrid architecture. | Variable – offers flexibility in balancing decentralization and scalability needs. |
Decentralized Identifiers (DIDs) and Verifiable Credentials (VCs)
Source: antiersolutions.com
Forget the days of relying on centralized authorities to manage your identity. Decentralized Identifiers (DIDs) and Verifiable Credentials (VCs) are revolutionizing how we prove who we are online, offering greater control and security. Think of it as getting your digital identity back – you’re in charge, not some faceless corporation.
DIDs are like your unique digital address, but instead of being controlled by a single entity, it’s decentralized, meaning it’s managed by you. This self-sovereign identity allows you to control what information you share and with whom. This is a game-changer for privacy and security, moving away from the vulnerabilities inherent in centralized systems. Imagine having a digital passport that only reveals the necessary information for each specific transaction, without exposing your entire identity. That’s the power of DIDs.
DID Functionality in Self-Sovereign Identity
DIDs enable self-sovereign identity by allowing individuals to own and manage their digital identities. This means you control which data points are shared and with whom. No more relying on a single entity like a social media platform or government agency to hold the keys to your digital identity. With a DID, you are the custodian of your own information. This level of control offers enhanced privacy and reduces the risk of identity theft or data breaches, as the data is not concentrated in a single, vulnerable point. For example, a user could use their DID to access a service without revealing unnecessary personal information, only proving their age or eligibility for a specific service.
Verifiable Credentials (VCs) for Secure Identity Verification
Verifiable Credentials are digital documents that prove specific attributes about an individual. Think of them as digital diplomas, driver’s licenses, or medical records, but with added security features. VCs are cryptographically secured, meaning they are tamper-proof and easily verifiable. This ensures that the information presented is authentic and hasn’t been altered. The verification process is also streamlined, allowing for quick and secure authentication without the need for extensive background checks. This technology offers a significant improvement over traditional methods, which often rely on easily forged documents or vulnerable databases.
Hypothetical University Student Record System using DIDs and VCs
Imagine a university using DIDs and VCs to manage student records. Each student would be issued a DID upon enrollment. This DID would act as their unique identifier across the university’s systems. To prove enrollment, the student could present a Verifiable Credential (VC) demonstrating their status. Similarly, other VCs could prove things like successful completion of courses, GPA, and even financial aid eligibility. The university could verify these credentials without accessing the student’s entire record, ensuring privacy while maintaining efficient record-keeping. This system enhances data security, protects student privacy, and streamlines administrative processes, reducing the risk of fraud and improving overall efficiency. The university would only need to verify the signature on the VC, not the entire content, making the process faster and more secure. Students retain control over their data, deciding what information to share with professors, employers, or other relevant parties.
Security and Privacy Aspects of Blockchain-based Identity
Blockchain technology offers a compelling alternative to traditional centralized identity management systems, promising enhanced security and privacy. However, it’s crucial to understand both the strengths and weaknesses inherent in this approach. While blockchain’s inherent immutability and cryptographic security offer significant advantages, potential vulnerabilities exist that require careful consideration and robust mitigation strategies.
The security of blockchain-based identity hinges on several factors, including the cryptographic algorithms used, the robustness of the consensus mechanism, and the overall design of the system. A well-designed system leverages the strengths of blockchain while addressing its inherent limitations.
Blockchain Security Implications
Blockchain’s decentralized nature inherently distributes trust, making it more resilient to single points of failure compared to centralized systems. The cryptographic hashing and digital signatures employed ensure data integrity and authenticity. However, vulnerabilities can still arise. For instance, private keys, which are essential for accessing and managing digital identities, must be meticulously protected against theft or compromise. A compromised private key grants an attacker complete control over the associated digital identity. Furthermore, vulnerabilities in smart contracts that govern identity management could be exploited. Rigorous auditing and security testing of smart contracts are vital to mitigating this risk. Another concern is the potential for 51% attacks on smaller, less established blockchain networks, where a malicious actor could potentially control the network and manipulate the identity data.
Vulnerabilities and Mitigation Strategies, The Role of Blockchain in Digital Identity Management
Several vulnerabilities exist within blockchain-based identity systems, necessitating proactive mitigation strategies. One significant vulnerability is the potential for phishing attacks targeting users to steal their private keys. Strong password management practices, multi-factor authentication, and user education campaigns are crucial for mitigating this risk. Another vulnerability lies in the potential for smart contract vulnerabilities, which can be exploited to manipulate or steal identity data. Thorough code audits and security testing are vital to identify and address such vulnerabilities before deployment. Finally, the reliance on specific cryptographic algorithms introduces the risk of future breakthroughs that could compromise the security of the system. Staying abreast of advancements in cryptography and updating algorithms as needed is essential.
Comparison of Privacy Implications
The privacy implications of blockchain-based identity differ significantly from centralized systems. Let’s compare:
- Data Control: Blockchain-based systems empower individuals with greater control over their data, as they hold their own private keys and can selectively share verifiable credentials. Centralized systems, conversely, grant control to the organization holding the data.
- Data Transparency: While blockchain transactions are publicly recorded, identity data itself can be encrypted and only revealed selectively through verifiable credentials, offering a degree of privacy not available in many centralized systems. Centralized systems often have less transparency regarding data usage and storage.
- Data Security: Blockchain’s cryptographic security and decentralized nature make it more resistant to data breaches than centralized systems, which are vulnerable to single points of failure and large-scale data breaches. However, as previously discussed, proper key management and secure smart contract development remain crucial.
- Data Portability: Blockchain allows for easier data portability, as individuals can easily transfer their verifiable credentials between different services and applications. Centralized systems often create data silos, making data transfer difficult and cumbersome.
Implementation and Case Studies
Blockchain’s potential in digital identity is exciting, but its real-world impact hinges on successful implementation. Numerous organizations are already leveraging blockchain technology to revolutionize identity management across various sectors, boosting efficiency and trust. Let’s dive into some compelling examples.
Several factors contribute to the success or failure of blockchain implementations. Careful consideration of scalability, interoperability, regulatory compliance, and user experience is crucial. A phased approach, starting with a pilot project in a specific area, often proves more effective than a large-scale, immediate rollout.
Healthcare: Secure Patient Data Management
The healthcare industry is ripe for disruption through blockchain’s secure and transparent data management capabilities. Imagine a system where patient medical records are securely stored on a blockchain, accessible only with the patient’s consent. This eliminates the risk of data breaches and simplifies the sharing of information between healthcare providers. For example, a hospital in Estonia has been using a blockchain-based system to manage electronic health records, ensuring data integrity and patient privacy. The system allows patients to control access to their records and share them securely with doctors and other healthcare providers. This significantly streamlines the process of obtaining and sharing crucial medical information, improving patient care and reducing administrative overhead.
Finance: Enhanced KYC/AML Compliance
Know Your Customer (KYC) and Anti-Money Laundering (AML) compliance are critical for financial institutions. Blockchain can streamline these processes by creating a shared, immutable record of customer identities. This eliminates the need for multiple identity verifications across different institutions, reducing costs and improving efficiency. Several fintech companies are now utilizing blockchain to verify customer identities, significantly reducing the time and resources required for compliance checks. This also helps in preventing fraudulent activities by creating a more robust and transparent system for verifying identities. The reduced duplication of effort also minimizes the risk of errors and discrepancies in customer data.
Government: Secure Citizen Identity Management
Governments worldwide are exploring the use of blockchain for secure citizen identity management. A blockchain-based system can provide citizens with greater control over their personal data, while also providing government agencies with a secure and reliable way to verify identities. For instance, some countries are exploring the use of blockchain to issue digital IDs, providing citizens with a secure and convenient way to access government services. This reduces the risk of identity theft and fraud, and simplifies the process of verifying identity for various government transactions. The immutable nature of blockchain ensures that identity information remains secure and tamper-proof, enhancing trust and transparency in government processes.
Improving Efficiency and Trust
Blockchain’s decentralized and immutable nature significantly improves efficiency and trust in identity verification processes. By eliminating the need for centralized authorities, blockchain enhances transparency and reduces the risk of fraud and data breaches. The shared, immutable ledger ensures that all transactions are recorded and verifiable, increasing accountability and reducing the likelihood of disputes. Furthermore, the automation capabilities of blockchain streamline processes, reducing manual effort and accelerating verification times. This translates to cost savings and improved user experience for individuals and organizations alike. The enhanced security and trust fostered by blockchain also contribute to a more robust and reliable identity management ecosystem.
Interoperability and Standardization
Imagine a world where your digital identity, securely stored on a blockchain, works seamlessly across different platforms and services – from logging into your bank account to accessing your healthcare records. This is the promise of interoperable blockchain-based identity systems, but achieving this requires careful consideration of standardization and overcoming significant technical hurdles. Without interoperability, we risk creating a fragmented landscape of incompatible systems, negating many of the benefits of blockchain technology for digital identity.
The core challenge lies in the diverse nature of blockchain technologies themselves. Different blockchains utilize varying consensus mechanisms, data structures, and programming languages. This inherent heterogeneity makes it difficult to establish a common framework for exchanging identity data and verifying credentials. Furthermore, integrating with existing legacy systems, which often lack the robust security and privacy features of blockchain, presents another layer of complexity. Successful interoperability demands a concerted effort from developers, standards bodies, and regulatory authorities to create a unified ecosystem.
Existing Standards and Initiatives
Several organizations are actively working to define standards and foster interoperability in the blockchain-based identity space. These efforts focus on creating common data formats, communication protocols, and security guidelines. For instance, the Decentralized Identifier (DID) specification, developed by the World Wide Web Consortium (W3C), provides a framework for creating and managing decentralized digital identities. This is complemented by the Verifiable Credentials (VC) data model, which enables the secure and verifiable exchange of identity attributes. The International Organization for Standardization (ISO) is also involved, developing standards related to blockchain technology and digital identity management. These initiatives, while still evolving, are crucial in laying the foundation for a more interconnected and interoperable ecosystem. The success of these initiatives hinges on widespread adoption by both technology providers and organizations utilizing blockchain-based identity systems. Without this collaborative effort, standardization efforts will fall short of their intended goals.
Future Directions of Standardization Efforts
Looking ahead, the focus will likely shift towards developing more sophisticated mechanisms for data governance and privacy preservation. This includes exploring techniques for selective disclosure of identity information, enabling individuals to control precisely what data is shared with specific entities. Furthermore, standardization efforts will need to address the challenges posed by emerging technologies, such as decentralized autonomous organizations (DAOs) and the metaverse, which are likely to reshape the digital identity landscape. Ultimately, the goal is to create a system that is not only interoperable but also user-centric, empowering individuals with greater control and transparency over their digital identities. One possible future direction could be the development of standardized APIs (Application Programming Interfaces) that allow different blockchain-based identity systems to communicate and exchange data seamlessly, much like how modern payment systems operate. This would simplify integration and encourage wider adoption of blockchain-based identity solutions. This would require a significant investment in research and development, along with close collaboration between stakeholders.
Scalability and Performance Considerations
Blockchain’s decentralized nature, while offering robust security, presents significant scalability challenges for digital identity management systems. The inherent limitations in transaction processing speed and storage capacity can hinder the adoption of blockchain solutions, especially when dealing with large-scale identity verification and credential management. Finding the right balance between security and performance is crucial for widespread acceptance.
The core issue lies in the blockchain’s consensus mechanism. Proof-of-Work (PoW) blockchains, known for their security, suffer from relatively low transaction throughput. Proof-of-Stake (PoS) mechanisms offer improvements, but scalability remains a critical concern as the number of users and transactions increases. This bottleneck can lead to increased latency, higher transaction fees, and a less responsive user experience, ultimately undermining the practical utility of the system.
Solutions for Enhanced Scalability
Several strategies are employed to address the scalability limitations of blockchain-based identity systems. These solutions aim to increase transaction throughput without compromising the security and decentralization principles that define blockchain technology.
- Sharding: This technique partitions the blockchain into smaller, more manageable shards, each processing transactions independently. This allows for parallel processing, significantly increasing transaction throughput. Imagine a large database divided into smaller, more easily searchable sections. Each shard can maintain its own consensus mechanism, leading to faster processing speeds. However, cross-shard communication needs careful consideration to maintain data consistency.
- Layer-2 Scaling Solutions: These solutions operate on top of the main blockchain, handling a large volume of transactions off-chain. Examples include state channels and sidechains. State channels allow multiple transactions to be bundled and settled on the main chain only when necessary, reducing the load on the main blockchain. Sidechains act as parallel blockchains that can process transactions independently, with occasional data synchronization with the main chain. Think of them as express lanes for transactions, bypassing the main highway congestion.
- Improved Consensus Mechanisms: Developing more efficient consensus mechanisms is a continuous area of research. Beyond PoW and PoS, other mechanisms like Practical Byzantine Fault Tolerance (PBFT) and Delegated Proof-of-Stake (DPoS) are being explored for their potential to improve scalability while maintaining security. These newer mechanisms aim to reduce the computational overhead and energy consumption associated with traditional consensus methods.
Comparative Performance Analysis of Scaling Solutions
A visual representation, in the form of a table, can help compare the performance characteristics of different scaling solutions. Note that the values are illustrative and can vary depending on specific implementation details and network conditions.
| Scaling Solution | Transaction Throughput (TPS) | Latency (ms) | Security | Complexity |
|---|---|---|---|---|
| No Scaling (e.g., Basic PoW) | 10-20 | 1000-5000 | High | Low |
| Sharding | 1000-10000 | 100-500 | Medium-High | High |
| Layer-2 (State Channels) | 1000-5000 | 10-100 | Medium-High | Medium |
| Layer-2 (Sidechains) | 500-5000 | 50-200 | Medium | Medium-High |
The table demonstrates that while basic PoW blockchains exhibit low throughput and high latency, scaling solutions like sharding and Layer-2 protocols significantly improve performance. However, these improvements often come with increased complexity and potential trade-offs in security. The choice of the optimal scaling solution depends on the specific requirements of the digital identity system, balancing performance needs with security and implementation complexity.
Ethical and Societal Implications: The Role Of Blockchain In Digital Identity Management
Blockchain’s application to digital identity management, while promising increased security and user control, presents a complex web of ethical and societal considerations. The decentralized nature, while beneficial in many ways, also introduces new challenges regarding accountability, bias, and the potential for misuse. Understanding these implications is crucial for responsible development and deployment of this technology.
The shift towards blockchain-based digital identity fundamentally alters the power dynamics surrounding personal data. This transition necessitates a careful examination of its impact on individual autonomy, societal trust, and the potential for exacerbation of existing inequalities.
Data Ownership and Control
Blockchain technology, in theory, empowers individuals with greater control over their digital identities. By storing identity data on a distributed ledger, individuals can theoretically manage and share their information selectively, granting access only to specific entities and for specific purposes. This contrasts sharply with centralized systems where data is often siloed and controlled by large corporations or governments. However, the practical reality is more nuanced. The technical complexity of managing private keys and interacting with decentralized systems can create barriers to access for less tech-savvy individuals, potentially widening the digital divide. Furthermore, the reliance on third-party services for managing and accessing DIDs could still leave individuals vulnerable to data breaches or manipulation if those services are compromised. Effective user education and accessible interfaces are crucial to ensure that the promise of increased user control translates into reality.
Bias and Discrimination
The algorithms and data used to create and manage digital identities on a blockchain can perpetuate or even amplify existing societal biases. For instance, if the initial data used to train AI systems for identity verification is skewed, the resulting system may unfairly discriminate against certain groups. Furthermore, the lack of transparency in some blockchain implementations could make it difficult to identify and address such biases. Robust auditing mechanisms and rigorous testing for bias are essential to mitigate these risks. Consider, for example, a system that uses facial recognition for identity verification—if the training data primarily features individuals from a particular ethnic background, the system may perform poorly for individuals from other backgrounds, leading to unfair rejection or denial of services.
Privacy and Surveillance
While blockchain can enhance privacy by limiting data access, the immutability of the blockchain also raises concerns about surveillance. Once data is recorded on the blockchain, it is difficult, if not impossible, to erase it. This raises questions about the potential for long-term tracking and monitoring of individuals, especially in the context of government-led identity systems. Careful consideration must be given to data minimization principles and the implementation of robust access control mechanisms to prevent unauthorized access and misuse of personal information. Furthermore, the use of pseudonyms or other anonymization techniques should be explored to balance the benefits of immutability with the need for privacy. The potential for linking seemingly anonymized data through sophisticated analysis techniques should also be considered and proactively addressed.
Ultimate Conclusion
Blockchain’s impact on digital identity management is undeniable. While challenges remain, the potential benefits – enhanced security, increased user control, and improved efficiency – are too significant to ignore. As the technology matures and standards solidify, we can expect to see a significant shift towards self-sovereign identity, empowering individuals and reshaping the landscape of digital interactions. The future of digital identity is decentralized, and it’s powered by blockchain.
