The Impact of Quantum Computing on Global Cryptography Standards: It’s the cryptographic apocalypse, or is it? Quantum computers, those mind-bending machines, are poised to shatter the foundations of our digital security. Algorithms that once seemed impenetrable – RSA, ECC – are suddenly vulnerable to attacks like Shor’s algorithm. This isn’t some far-off sci-fi threat; experts are predicting a real and present danger, forcing a global scramble to create new, quantum-resistant cryptography. The race is on, and the stakes couldn’t be higher.
Imagine a world where sensitive data – financial transactions, medical records, national secrets – is suddenly exposed. That’s the chilling reality quantum computing presents. We’re talking about a potential for massive data breaches, societal chaos, and a complete reshaping of how we secure information. The transition to post-quantum cryptography is a monumental undertaking, involving global cooperation, massive infrastructure overhauls, and potentially crippling costs. This isn’t just a tech problem; it’s a societal one.
Current Cryptographic Algorithms and Quantum Threats
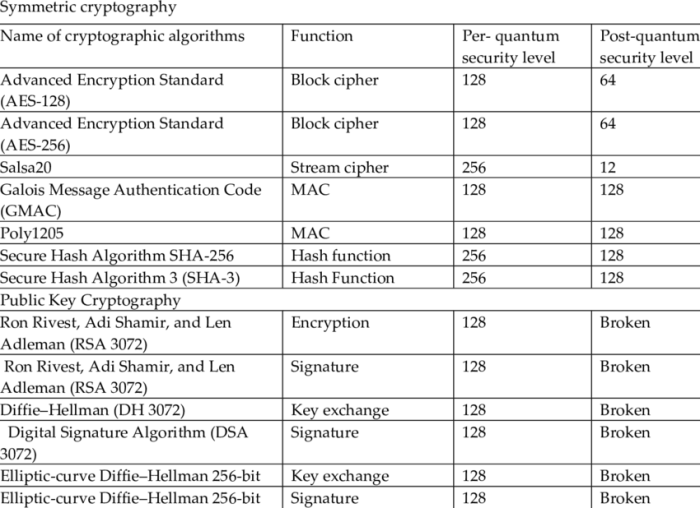
Source: researchgate.net
The rise of quantum computing presents a significant challenge to the foundations of modern cryptography. Algorithms that currently secure our digital world, from online banking to national security communications, could become vulnerable to attacks from sufficiently powerful quantum computers. Understanding these vulnerabilities and exploring alternative solutions is crucial for maintaining digital security in the quantum era.
Currently, widely used public-key cryptographic algorithms like RSA and Elliptic Curve Cryptography (ECC) rely on mathematical problems that are computationally hard for classical computers to solve. However, Shor’s algorithm, a quantum algorithm developed by Peter Shor, efficiently solves these problems, rendering these algorithms insecure against sufficiently powerful quantum computers. This poses a severe threat to the confidentiality, integrity, and authenticity of digital information.
Quantum computing’s potential to crack current encryption is a major headache for global security. But the shift towards more secure systems might ironically be accelerated by advancements in AI, like those explored in this insightful article on How Artificial Intelligence is Shaping the Future of Online Shopping , where AI’s role in enhancing e-commerce security is highlighted. Ultimately, the race is on to develop quantum-resistant cryptography before the threat becomes reality.
Vulnerabilities of RSA and ECC to Quantum Attacks
RSA’s security rests on the difficulty of factoring large numbers into their prime components. ECC’s security relies on the difficulty of solving the elliptic curve discrete logarithm problem. Shor’s algorithm efficiently solves both these problems, allowing a quantum computer to break RSA and ECC encryption relatively quickly. The larger the key size, the longer it takes a classical computer to break the encryption, but a sufficiently powerful quantum computer could break even very large key sizes relatively swiftly. This means that data encrypted today using RSA or ECC could be decrypted in the future when sufficiently advanced quantum computers become available.
Timeline for Quantum Threats to Cryptographic Algorithms
Predicting the exact timeline for when quantum computers will pose a realistic threat is challenging. Experts are divided, but some estimates suggest that within the next 10-20 years, quantum computers capable of breaking widely used cryptographic algorithms could emerge. This is not a precise prediction; the development of quantum computing technology is complex and subject to unforeseen breakthroughs or setbacks. However, the potential threat is real enough to warrant immediate action. Consider, for example, the potential impact on long-term data security – documents, financial records, and sensitive communications encrypted today might become vulnerable to decryption in the future.
Post-Quantum Cryptographic Algorithms: A Comparison
Recognizing the looming threat, researchers are actively developing post-quantum cryptographic algorithms—algorithms resistant to attacks from both classical and quantum computers. Several promising approaches exist, each with its strengths and weaknesses. Choosing the right algorithm involves careful consideration of security level, performance overhead, and implementation complexity.
| Algorithm Name | Security Level | Performance | Implementation Complexity |
|---|---|---|---|
| Lattice-based (e.g., CRYSTALS-Kyber) | High | Relatively good | Moderate |
| Code-based (e.g., Classic McEliece) | High | Relatively slow | High |
| Multivariate (e.g., Rainbow) | Moderate to High | Moderate | Moderate to High |
| Hash-based (e.g., SPHINCS+) | High | Relatively slow | High |
The Impact on Data Security and Privacy
The advent of quantum computing presents a chilling prospect for global data security. Its potential to shatter current encryption methods poses a profound threat to the confidentiality and integrity of sensitive information across various sectors, potentially leading to unprecedented levels of data breaches and societal disruption. The implications are far-reaching, impacting everything from financial transactions to national security.
Current encryption algorithms, the bedrock of online security, rely on mathematical problems deemed computationally intractable for classical computers. However, quantum computers, with their fundamentally different approach to computation, could solve these problems relatively quickly, rendering many widely used encryption techniques obsolete. This presents a clear and present danger to the vast amounts of sensitive data stored and transmitted digitally.
Consequences of Quantum-Enabled Decryption for Sensitive Data
The ability of quantum computers to crack current encryption spells disaster for sensitive data. Financial transactions, reliant on secure communication channels, become vulnerable to fraud and theft on a massive scale. Medical records, containing highly personal and often legally protected information, could be exposed, leading to identity theft and potential harm to patients. Government secrets, crucial for national security, could fall into the wrong hands, potentially destabilizing geopolitical landscapes. The sheer volume of data at risk is staggering, and the potential for misuse is terrifying. Consider, for instance, the potential compromise of a nation’s entire tax database or the exposure of classified military communications.
Potential for Large-Scale Data Breaches and Societal Impact
The successful deployment of quantum computers capable of breaking current encryption standards could trigger a cascade of large-scale data breaches. Imagine a scenario where a malicious actor gains access to a quantum computer powerful enough to decrypt the encrypted communications of a major financial institution. This could lead to the theft of billions of dollars, causing widespread financial instability and eroding public trust in financial systems. The societal consequences would be profound, impacting everything from economic stability to public confidence in digital security. The fallout could extend to political instability, depending on the scale of the breach and the sensitivity of the compromised data. This is not mere speculation; experts are already warning of this potential threat and calling for proactive measures.
Hypothetical Scenario: Quantum Attack on a Major Financial Institution
Let’s imagine a hypothetical scenario involving Global Bank, a major multinational financial institution. A sophisticated state-sponsored actor gains access to a powerful quantum computer and targets Global Bank’s encrypted transaction data. Using quantum algorithms, they successfully decrypt years’ worth of transactions, gaining access to sensitive customer information, including account numbers, balances, and transaction histories. The resulting breach leads to massive fraud, significant financial losses for the bank and its customers, a dramatic drop in the bank’s stock value, and widespread public panic and distrust. Lawsuits ensue, regulatory investigations are launched, and the bank’s reputation is severely tarnished. This scenario highlights the potentially catastrophic consequences of a successful quantum attack on a critical infrastructure component like a major financial institution.
Industries Most Vulnerable to Quantum Attacks
Several industries are particularly vulnerable to quantum attacks due to their reliance on sensitive data and sophisticated digital infrastructure. The financial sector, as illustrated above, is extremely vulnerable due to the sheer volume of financial transactions and the potential for large-scale financial losses. The healthcare industry, with its trove of sensitive patient data, is another prime target. Government agencies, holding national security secrets and critical infrastructure information, face potentially devastating consequences from quantum-enabled breaches. The defense and intelligence communities are also highly vulnerable, as their systems often rely on heavily encrypted communications and data storage. The high value of the data held by these sectors makes them lucrative targets for quantum-powered attacks.
Global Standardization Efforts and Challenges
The race is on to secure our digital future against the looming threat of quantum computers. As quantum computing power advances, the cryptographic algorithms safeguarding our data are increasingly vulnerable. This necessitates a global, coordinated effort to establish new, quantum-resistant cryptographic standards—a monumental task fraught with technical, political, and logistical hurdles.
The development and implementation of post-quantum cryptography (PQC) standards is a complex undertaking involving numerous international organizations and national governments. The urgency stems from the potential for widespread data breaches if current cryptographic systems are compromised. Success requires a delicate balance between technological innovation, international collaboration, and the practical considerations of implementation across diverse systems and infrastructures.
Key Players in Post-Quantum Cryptography Standardization, The Impact of Quantum Computing on Global Cryptography Standards
Several key players are driving the development and implementation of PQC standards. The National Institute of Standards and Technology (NIST) in the United States has been at the forefront, leading a highly publicized competition to select quantum-resistant algorithms. Other important organizations include the International Organization for Standardization (ISO), which works to create internationally agreed-upon standards, and various national standardization bodies like the European Telecommunications Standards Institute (ETSI). These organizations work collaboratively, though with varying approaches, to ensure the adoption of secure and interoperable PQC standards worldwide. The collaborative nature is crucial to prevent a fragmented landscape of incompatible cryptographic systems.
Comparison of Standardization Approaches
Different nations and organizations have adopted different approaches to PQC standardization. NIST’s approach, for instance, involved a multi-stage competition, rigorously evaluating numerous algorithms based on their security, performance, and implementation characteristics. This highly competitive process aimed to select the most robust and versatile algorithms. Other organizations may adopt different evaluation criteria or processes, leading to potentially varied outcomes. The ISO’s approach, while collaborative, involves a more deliberative process, potentially resulting in slower but broader consensus. This diversity in approach underscores the challenges of achieving global uniformity.
Challenges in Achieving Global Consensus
Achieving global consensus on PQC standards presents significant challenges. Differing national priorities, technical viewpoints, and implementation capabilities can hinder progress. The need to balance security with performance and ease of implementation across various systems further complicates the process. Concerns about intellectual property rights and the potential for backdoors in algorithms also require careful consideration. Furthermore, the transition to new standards requires significant investment and coordination across industries, posing a logistical hurdle of considerable scale. For example, the widespread adoption of new cryptographic algorithms within existing infrastructure necessitates extensive testing and compatibility assessments.
Timeline of Significant Milestones
A timeline illustrating key milestones in PQC standardization highlights the ongoing and dynamic nature of this effort.
- 2016: NIST initiates its post-quantum cryptography standardization process.
- 2017-2020: Multiple rounds of algorithm submissions and evaluations occur within the NIST competition.
- 2022: NIST announces its first set of standardized quantum-resistant algorithms.
- Ongoing: Continued evaluation, refinement, and adoption of PQC standards globally by various organizations and governments.
This timeline demonstrates the significant progress made, yet also emphasizes the ongoing nature of the standardization effort and the need for continued vigilance and collaboration. The process is iterative, with ongoing evaluation and potential revisions as the field of quantum computing evolves.
Migration Strategies and Implementation Costs: The Impact Of Quantum Computing On Global Cryptography Standards
The shift to post-quantum cryptography (PQC) isn’t a simple software update; it’s a complex, multi-stage process demanding careful planning and significant resource allocation. Organizations of all sizes face unique challenges, from technical hurdles to budgetary constraints. Understanding these challenges and developing effective migration strategies is crucial for ensuring continued data security in the quantum era.
The migration from current cryptographic systems to PQC involves a phased approach, encompassing assessment, selection, implementation, and ongoing monitoring. This isn’t a one-size-fits-all solution; the specific steps and timelines will vary based on an organization’s size, infrastructure, and the sensitivity of the data it handles. Furthermore, the cost-benefit analysis will differ significantly depending on these factors.
Technical Challenges and Resource Requirements of PQC Migration
Migrating to PQC presents several technical challenges. These include integrating new algorithms into existing systems, ensuring compatibility with legacy infrastructure, and managing the increased computational overhead associated with some PQC algorithms. Resource requirements encompass skilled personnel with expertise in cryptography and cybersecurity, substantial computing power for testing and implementation, and dedicated budget for software and hardware upgrades. For example, a large financial institution might need to invest in specialized hardware to accelerate PQC computations, while a smaller business might rely on cloud-based solutions. The process also requires rigorous testing to validate the security and performance of the new cryptographic systems. This includes penetration testing and vulnerability assessments to identify and mitigate any weaknesses before deployment.
Cost-Benefit Analysis of PQC Implementation Across Different Organizations
The cost of implementing PQC varies significantly depending on the organization’s size and complexity. Small businesses may face relatively lower costs, primarily focused on software upgrades and training. However, they may also struggle to justify the investment if their data isn’t highly sensitive. Large corporations and governments, on the other hand, will face significantly higher costs due to the scale of their operations and the need for extensive system-wide upgrades. They may need to invest in new hardware, specialized expertise, and extensive testing, potentially incurring millions or even billions of dollars in costs. The benefits, however, are equally substantial, ranging from protecting sensitive data from future quantum computer attacks to maintaining customer trust and complying with regulatory requirements. The cost-benefit ratio should be carefully evaluated based on the potential losses from a data breach versus the cost of migration. For instance, a government agency handling classified information faces catastrophic consequences from a breach, making the investment in PQC a necessity.
Step-by-Step Guide: Migrating an E-commerce Platform to PQC
Let’s consider a hypothetical e-commerce platform. A step-by-step migration to PQC might look like this:
- Assessment: Identify all cryptographic components used in the platform (SSL/TLS, digital signatures, etc.) and assess their vulnerability to quantum attacks.
- Algorithm Selection: Choose appropriate PQC algorithms based on security requirements and performance considerations. NIST’s post-quantum cryptography standardization process provides guidance here.
- Proof-of-Concept: Implement the chosen algorithms in a test environment to evaluate their performance and integration with existing systems.
- Pilot Implementation: Deploy the PQC solution on a small subset of the platform to test its functionality and stability in a real-world setting.
- Full-Scale Deployment: Gradually roll out the PQC solution across the entire platform, ensuring minimal disruption to users.
- Monitoring and Maintenance: Continuously monitor the system for security vulnerabilities and performance issues, and update the PQC implementation as needed.
This process requires close collaboration between IT professionals, security experts, and developers. Thorough testing and a phased rollout are crucial to minimize disruption and ensure a smooth transition to PQC. The cost will depend on the platform’s complexity and the resources required for each step.
The Role of Quantum-Resistant Hardware
The looming threat of quantum computers breaking current encryption standards necessitates a proactive approach to securing our digital future. This involves not just developing new algorithms, but also integrating them into robust, quantum-resistant hardware. This hardware acts as the physical foundation for securing data, offering a tangible layer of defense against quantum attacks. Its development and widespread adoption are crucial for maintaining data integrity and privacy in the post-quantum era.
The integration of quantum-resistant hardware into existing and future systems presents a significant technological challenge, requiring substantial investment in research and development. The performance impact of this specialized hardware on post-quantum cryptographic systems is a key consideration. While the algorithms themselves might be computationally intensive, hardware acceleration can significantly improve performance, making post-quantum cryptography practical for widespread deployment. Furthermore, the security offered by dedicated hardware goes beyond just algorithmic strength; it can provide protection against side-channel attacks, a significant vulnerability in software-only implementations.
Quantum-Resistant Hardware Architectures
Several approaches exist for building quantum-resistant hardware. One strategy focuses on specialized integrated circuits (ASICs) designed specifically for accelerating post-quantum algorithms. These ASICs offer optimized performance and power efficiency but can be expensive to develop and manufacture, limiting their accessibility. Another approach involves using Field-Programmable Gate Arrays (FPGAs), offering greater flexibility and reconfigurability. FPGAs allow for quicker adaptation to new algorithms and security updates, making them a more agile solution. However, their performance may not match the optimization of ASICs. A third approach involves leveraging existing CPU and GPU architectures, modifying them through software and firmware updates to enhance their ability to handle post-quantum algorithms. This approach is more cost-effective in the short term but might not offer the same level of security or performance optimization as specialized hardware.
Performance and Security Trade-offs
The choice between different quantum-resistant hardware approaches involves careful consideration of performance and security trade-offs. ASICs generally offer superior performance but lack the flexibility of FPGAs. FPGAs, while adaptable, may not reach the same peak performance levels. Software-based solutions on existing hardware offer the most accessible and cost-effective approach initially, but their security might be compromised if vulnerabilities in the underlying architecture are exploited. The ideal solution often depends on the specific application and the level of security required. For example, high-security government applications might favor ASICs, while less sensitive commercial applications might opt for FPGAs or software-based solutions.
Mitigating Quantum Computing Attacks
Quantum-resistant hardware significantly mitigates the risks associated with quantum computing attacks by providing a physical layer of protection. This hardware can perform cryptographic operations in a secure environment, minimizing the risk of side-channel attacks that exploit timing or power consumption patterns. Furthermore, the specialized design of quantum-resistant hardware can be optimized to resist specific types of quantum attacks, providing a higher level of security than software-only implementations. For instance, hardware-based implementations can incorporate countermeasures against fault injection attacks, which attempt to manipulate the hardware’s behavior to extract cryptographic keys. This layered approach, combining robust algorithms with secure hardware, creates a more resilient defense against quantum threats.
Future Research Directions and Open Questions
The transition to post-quantum cryptography is a marathon, not a sprint. While significant progress has been made, numerous research avenues remain unexplored, promising both exciting breakthroughs and daunting challenges. Understanding these areas is crucial for building a truly secure cryptographic future resistant to the looming threat of quantum computers.
The field of post-quantum cryptography is actively evolving, with researchers constantly refining existing algorithms and exploring entirely new approaches. This dynamic landscape necessitates a continuous evaluation of the strengths and weaknesses of different systems, ensuring that the chosen standards are robust and adaptable to future advancements in both quantum computing and cryptanalysis.
Key Research Areas in Post-Quantum Cryptography
Research currently focuses on improving the efficiency and security of existing post-quantum algorithms. This includes optimizing their performance on various hardware platforms, developing more efficient key generation and verification methods, and rigorously analyzing their resistance to known and potential attacks. For instance, significant effort is dedicated to reducing the key sizes of lattice-based cryptography to improve performance without compromising security. Another area of focus is the development of more sophisticated side-channel attack countermeasures to protect implementations from physical attacks.
Potential Breakthroughs and Their Impact
A major potential breakthrough lies in the discovery of entirely new cryptographic primitives based on fundamentally different mathematical problems. This could lead to algorithms with superior performance and security characteristics compared to the current contenders. Imagine, for example, a new algorithm that achieves the security level of current RSA with a fraction of the computational overhead – this would revolutionize secure communication across various platforms. Furthermore, advancements in quantum-resistant hardware could dramatically accelerate the adoption of post-quantum cryptography, making it practical for resource-constrained devices.
Challenges in Ensuring Long-Term Security
Ensuring the long-term security of post-quantum cryptographic systems presents considerable challenges. The most significant is the potential for unforeseen vulnerabilities to emerge as quantum computing technology advances. Even algorithms that appear secure today might prove vulnerable to future, more powerful quantum computers or sophisticated cryptanalytic techniques. Additionally, the standardization process itself faces challenges, including balancing security, performance, and interoperability requirements. The complexity of implementing and managing post-quantum cryptography across diverse systems also poses a major hurdle. The lack of standardized implementation guidelines and the potential for compatibility issues across different systems will hinder the transition.
Open Research Questions
The interaction between quantum computing and cryptography presents several open research questions:
- What are the optimal strategies for migrating to post-quantum cryptography while minimizing disruption and cost?
- How can we effectively evaluate the long-term security of post-quantum algorithms against future quantum attacks?
- What are the most efficient and secure ways to implement post-quantum cryptography on resource-constrained devices?
- How can we develop robust and efficient key management systems for post-quantum cryptography?
- What are the implications of quantum computing for other cryptographic primitives, such as digital signatures and hash functions?
Last Point
The looming threat of quantum computing isn’t just a tech problem; it’s a global challenge demanding immediate attention. While the transition to post-quantum cryptography will be complex and expensive, the alternative – a world of easily compromised data – is far more costly. The ongoing standardization efforts, the development of quantum-resistant hardware, and continued research are all crucial steps in securing our digital future. The race to quantum-proof our world is on, and the outcome will shape the future of security for generations to come. Are we ready?
