The Future of Digital Privacy in an Increasingly Connected World is a conversation we desperately need to have. Our digital lives are more intertwined than ever, leaving a trail of data wherever we go. From the mundane to the deeply personal, our information is constantly collected, analyzed, and often, used in ways we don’t fully understand. This exploration dives into the evolving landscape of data collection, the implications of emerging technologies, the role of legislation, and what we, as individuals, can do to protect our digital selves.
We’ll examine how companies, both subtly and overtly, gather our data across various industries – social media, finance, healthcare – and the impact of the Internet of Things (IoT) on this ever-growing data deluge. We’ll also unpack the privacy challenges posed by AI, blockchain, and biometric data, analyzing the potential benefits and drawbacks of these powerful technologies. Finally, we’ll explore how legislation, user awareness, and innovative privacy-preserving technologies are shaping the future of digital privacy.
The Evolving Landscape of Data Collection
The digital age has fundamentally reshaped how we interact with the world, leaving an indelible trail of data in its wake. Companies, large and small, are increasingly sophisticated in their methods of collecting this data, leveraging it for targeted advertising, personalized services, and a myriad of other purposes. Understanding the evolving landscape of data collection is crucial for navigating the complexities of digital privacy in today’s hyper-connected world.
Current Data Collection Methods
Companies employ a range of techniques to gather user data, some overt and others far more subtle. Overt methods include directly asking users for information through forms, surveys, or app permissions. This is often presented as a necessary step for accessing services or features. Covert methods, however, are far more insidious. These include tracking user behavior through cookies and website analytics, collecting metadata from communications, and using sophisticated algorithms to infer personal information from publicly available data. For instance, a user’s online browsing history, combined with their social media activity, can reveal a wealth of personal details, even without explicit consent. The scale and sophistication of these methods are constantly evolving, making it increasingly difficult for individuals to maintain control over their own data.
Emerging Technologies and Their Privacy Implications: The Future Of Digital Privacy In An Increasingly Connected World
The digital revolution has ushered in an era of unprecedented technological advancements, fundamentally altering how we interact, communicate, and conduct our lives. This rapid evolution, however, presents a complex tapestry of opportunities and challenges, particularly concerning the protection of our digital privacy. Emerging technologies like artificial intelligence, blockchain, and biometric systems offer immense potential, but their implementation also raises critical questions about data security and individual liberties. Understanding these implications is crucial to navigating this increasingly connected world responsibly.
Artificial Intelligence and Machine Learning Algorithms: Privacy Challenges
AI and ML algorithms are transforming various sectors, from healthcare to finance, but their reliance on vast datasets raises significant privacy concerns. These algorithms learn from data, often including sensitive personal information. The process of training these algorithms can inadvertently expose patterns and correlations in the data that could compromise individual privacy. For instance, an AI system trained on medical records might inadvertently reveal a patient’s identity through seemingly innocuous data points. Furthermore, the opacity of some complex algorithms – often referred to as “black boxes” – makes it difficult to understand how decisions are made and what data is used, hindering accountability and transparency. Bias in the training data can also lead to discriminatory outcomes, further exacerbating privacy and fairness concerns.
Blockchain Technology: Impact on Data Security and Privacy
Blockchain technology, the foundation of cryptocurrencies like Bitcoin, offers a decentralized and transparent approach to data management. Its inherent security features, such as cryptographic hashing and distributed ledger technology, could potentially enhance data security and privacy. By eliminating central points of failure and providing immutable records, blockchain could reduce the risk of data breaches and unauthorized access. However, the public nature of many blockchain implementations means that data, while secure, may not be private. Moreover, the complexity of blockchain technology and the lack of standardized regulations present challenges to its widespread adoption for privacy-sensitive applications.
Biometric Data Collection and Usage: Privacy Risks
Biometric data, such as fingerprints, facial recognition, and iris scans, offers unique identifiers for authentication and verification. While convenient, the collection and use of this sensitive data present substantial privacy risks. Biometric data is inherently irreplaceable; if compromised, it cannot be easily changed or revoked, unlike passwords. The potential for misuse, such as unauthorized surveillance or identity theft, is significant. Furthermore, the lack of consistent regulations and standards governing the collection, storage, and use of biometric data leaves individuals vulnerable to exploitation. Concerns around data accuracy and potential biases embedded in biometric systems further complicate the picture.
Potential Benefits and Drawbacks of Emerging Technologies Regarding User Privacy
The following list summarizes the potential benefits and drawbacks of each technology concerning user privacy:
- Artificial Intelligence and Machine Learning:
- Benefits: Personalized services, improved security through anomaly detection, medical diagnosis advancements.
- Drawbacks: Data breaches, discriminatory outcomes due to biased data, lack of transparency in decision-making processes.
- Blockchain Technology:
- Benefits: Enhanced data security, increased transparency, reduced risk of data breaches.
- Drawbacks: Data may not be truly private in public blockchains, complexity of implementation, lack of standardized regulations.
- Biometric Data Collection and Usage:
- Benefits: Enhanced security and authentication, convenient user experience.
- Drawbacks: Irreplaceable data, potential for misuse and identity theft, lack of consistent regulations and standards.
The Role of Legislation and Regulation
The digital world’s rapid expansion has outpaced the development of comprehensive global privacy regulations. While numerous laws aim to protect personal data, their effectiveness varies widely, creating a complex and often fragmented landscape. Understanding these regulations, their limitations, and potential future frameworks is crucial for navigating the evolving challenges of digital privacy.
Governments worldwide are grappling with the need to balance individual privacy rights with the economic benefits of data-driven innovation. This tension is evident in the varying approaches taken to regulate data collection, use, and sharing. A critical analysis of existing legislation and a consideration of future legal frameworks are vital to ensure a secure and responsible digital future.
Navigating the future of digital privacy in our hyper-connected world demands a serious look at data usage. The implications are huge, extending even to areas like disaster prediction; the accuracy of forecasting, as discussed in this insightful article on The Role of Machine Learning in Predicting Natural Disasters , relies heavily on data analysis. Ultimately, responsible data handling is crucial, both for personal privacy and for the effectiveness of life-saving technologies.
Key Global Privacy Regulations
Several landmark regulations have emerged globally, each with its unique strengths and weaknesses. The General Data Protection Regulation (GDPR) in the European Union, for example, sets a high bar for data protection, granting individuals significant control over their personal information. In contrast, the California Consumer Privacy Act (CCPA) in the United States, while influential, offers a less stringent framework. Other notable regulations include Brazil’s LGPD (Lei Geral de Proteção de Dados) and Canada’s PIPEDA (Personal Information Protection and Electronic Documents Act). These regulations differ significantly in their scope, enforcement mechanisms, and the rights they afford to individuals. For instance, the GDPR’s extraterritorial reach impacts companies globally, while the CCPA focuses primarily on California residents.
Effectiveness of Regulations Across Jurisdictions
The GDPR’s impact has been substantial, leading to increased awareness of data privacy and prompting organizations to reassess their data handling practices. However, enforcement remains a challenge, with fines levied against companies for non-compliance varying considerably. The CCPA, while less comprehensive, has spurred similar changes within California and influenced other states considering similar legislation. The effectiveness of these regulations is often measured by factors such as the number of complaints filed, fines imposed, and changes in organizational data practices. However, a truly effective measure requires a holistic approach, considering both individual rights and the broader economic and social impacts. The success of these regulations often hinges on effective enforcement mechanisms and the level of cooperation from both businesses and individuals.
Challenges in Enforcing Privacy Regulations in a Globalized Digital Environment
Enforcing privacy regulations across borders presents significant challenges. The ease with which data can be transferred and processed across jurisdictions makes it difficult to pinpoint responsibility and ensure consistent application of the law. Jurisdictional conflicts, differing legal interpretations, and the lack of international harmonization complicate enforcement efforts. Furthermore, the rapidly evolving technological landscape constantly introduces new challenges, such as the use of artificial intelligence and the increasing sophistication of data tracking techniques. These developments often outpace the ability of lawmakers to create and enforce appropriate regulations. The sheer scale of data flows and the decentralized nature of the internet further exacerbate these difficulties. Consider the challenge of tracking data across multiple cloud servers located in different countries. This necessitates international collaboration and harmonization of data privacy laws.
A Hypothetical Legal Framework for Future Digital Privacy
A future-proof legal framework for digital privacy should prioritize a few key principles: data minimization, purpose limitation, and user consent. It would necessitate a robust, globally harmonized approach, perhaps based on a set of core principles that individual nations could adapt to their specific contexts. Enforcement mechanisms should be strengthened through international cooperation and the establishment of independent regulatory bodies with cross-border authority. This framework should also anticipate and address the challenges posed by emerging technologies like AI and blockchain, ensuring that technological innovation does not come at the expense of individual privacy. A crucial aspect would be the development of standardized data privacy impact assessments, allowing organizations to proactively identify and mitigate privacy risks. Finally, the framework must promote transparency and empower individuals with greater control over their personal data. Imagine a world where individuals have a single, easily accessible digital dashboard that allows them to manage their data preferences across different platforms and services. This hypothetical framework aims for a balance between fostering innovation and safeguarding fundamental privacy rights in an increasingly interconnected world.
User Awareness and Empowerment
In a world saturated with data collection, individual understanding and control over personal information are paramount. Empowering users to protect their digital privacy isn’t just a matter of technical know-how; it’s about fostering a culture of informed consent and responsible data handling. This requires a multi-pronged approach encompassing education, transparency, and accessible tools.
Educating users about digital privacy risks and best practices involves more than simply distributing pamphlets. It necessitates a sustained effort to demystify complex technological concepts and translate them into easily digestible information. This includes highlighting the potential consequences of data breaches, explaining how personal information is used and shared online, and providing clear, actionable steps for mitigation.
Strategies for Educating Users
Effective user education requires a diverse approach, utilizing various communication channels and formats to reach a wide audience. This includes incorporating digital privacy education into school curricula, creating engaging online resources and interactive tutorials, and partnering with influencers and community leaders to spread awareness. Government agencies and non-profit organizations play a crucial role in developing and disseminating these educational materials, ensuring they are accurate, accessible, and tailored to different demographics and levels of technical expertise. Furthermore, simplifying privacy policies and making them easily understandable is crucial. Instead of lengthy legal jargon, clear, concise summaries in plain language are needed.
The Importance of User Consent and Control
User consent should be freely given, specific, informed, and unambiguous. This means individuals should understand exactly what data is being collected, how it will be used, and who will have access to it. Furthermore, users should have the ability to easily withdraw their consent at any time, and to access, correct, or delete their data. The principle of data minimization dictates that only necessary data should be collected, and its retention should be limited to the purpose for which it was obtained. Empowering users with control over their data is not just a matter of ethics; it’s a fundamental right in an increasingly data-driven world.
Enhancing User Transparency Regarding Data Usage
Transparency in data usage involves clearly communicating to users how their data is being collected, processed, and used. This goes beyond simply providing a privacy policy; it means actively informing users about specific instances of data usage, providing clear explanations of data sharing practices, and allowing users to easily access their own data. Companies should adopt proactive measures to inform users about any changes in their data handling practices. Regular audits and independent assessments of data practices can build trust and demonstrate commitment to user privacy.
Tools and Technologies for Protecting Online Privacy, The Future of Digital Privacy in an Increasingly Connected World
Several tools and technologies empower users to take control of their digital privacy. These include privacy-focused search engines, encrypted messaging apps, and VPNs (Virtual Private Networks).
Using a VPN masks your IP address, making it more difficult for websites and trackers to identify your location and online activity. This adds an extra layer of security and anonymity when browsing the internet.
Encrypted messaging apps, like Signal, use end-to-end encryption, ensuring that only the sender and recipient can read the messages. This protects your communications from interception by third parties.
Privacy-focused search engines prioritize user privacy by not tracking search queries or personal information. They offer a more private alternative to mainstream search engines.
These tools, while not foolproof, significantly enhance user privacy by providing more control over data collection and usage. Their adoption is crucial in mitigating the risks associated with increased online connectivity.
The Future of Privacy-Preserving Technologies

Source: bigid.com
The digital age’s relentless march toward hyper-connectivity presents a stark challenge: how to balance the immense benefits of data analysis with the fundamental right to privacy. Fortunately, a new generation of privacy-preserving technologies is emerging, promising a future where data-driven innovation doesn’t come at the expense of individual freedoms. These technologies offer sophisticated methods to analyze data without compromising the confidentiality of the individual records within.
Privacy-preserving technologies are crucial for maintaining trust in data-driven systems and ensuring responsible data usage. Their development and implementation are not merely technical exercises but represent a vital step towards a more equitable and secure digital future. Let’s explore some of the most promising advancements.
Differential Privacy
Differential privacy is a technique that adds carefully calibrated noise to data sets, making it statistically difficult to identify individual records while preserving the overall statistical properties of the data. Imagine a survey asking about income. With differential privacy, the responses would be slightly altered randomly, making it nearly impossible to pinpoint any single person’s income, yet researchers could still draw accurate conclusions about the overall income distribution within the population. The amount of noise added is carefully calculated to balance the need for privacy with the accuracy of the analysis. This method is already being used by organizations like Google and Apple to release aggregate data about their users’ behavior without revealing specific individual information.
Federated Learning
Federated learning allows multiple parties to collaboratively train a shared machine learning model without exchanging their local data. Think of it like this: several hospitals want to train a model to diagnose a disease, but sharing patient records directly is impossible due to privacy regulations. With federated learning, each hospital trains a model on its own data, then only the model’s updates (not the data itself) are shared with a central server to create a combined, improved model. This approach significantly enhances privacy by keeping sensitive data decentralized. Google uses federated learning to improve its Gboard keyboard’s predictive text functionality without accessing users’ typing data directly.
Homomorphic Encryption
Homomorphic encryption allows computations to be performed on encrypted data without requiring decryption first. This is like being able to add two numbers together while they are still locked in a safe – you get the result (the sum) without ever having to open the safe and see the individual numbers. This is incredibly useful for cloud computing, allowing sensitive data to be stored and processed remotely without compromising security. While still relatively nascent, its potential to revolutionize secure data processing is immense. For example, it could enable secure medical data analysis in the cloud without exposing patient records.
Decentralized Identity Systems
Decentralized identity systems, such as those based on blockchain technology, aim to give users more control over their personal data. Instead of relying on centralized authorities (like Facebook or Google) to manage identities, users can manage their own digital identities and selectively share specific attributes with different services. This approach reduces the risk of large-scale data breaches and empowers users with greater autonomy over their personal information. Examples include self-sovereign identity initiatives that are emerging globally, aiming to provide users with greater control and transparency over their digital identities.
Zero-Knowledge Proofs
Zero-knowledge proofs allow one party (the prover) to prove to another party (the verifier) that a statement is true without revealing any information beyond the truth of the statement itself. Imagine proving you know the password to a specific account without actually revealing the password. A zero-knowledge proof would allow you to demonstrate that you possess the correct password by successfully completing a series of cryptographic challenges, without ever disclosing the password itself. This technology has applications in various fields, from secure authentication systems to anonymous voting schemes. For instance, a user could prove their age to access age-restricted content without disclosing their exact birthdate.
Ultimate Conclusion
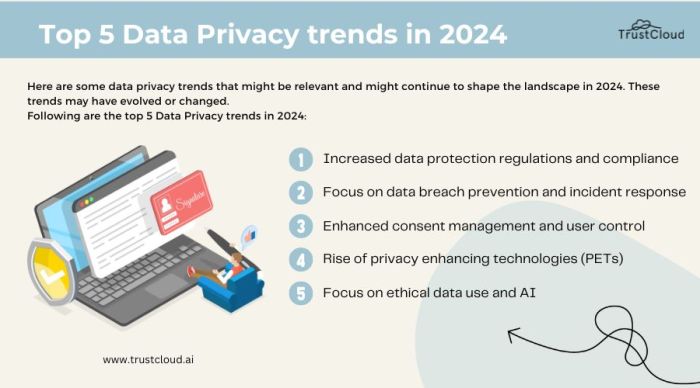
Source: trustcloud.ai
Ultimately, the future of digital privacy hinges on a multifaceted approach. Stronger legislation and regulation are crucial, but equally important is user education and empowerment. We need to understand the risks, demand transparency, and utilize the tools available to protect our data. The development and adoption of privacy-preserving technologies like differential privacy and decentralized identity systems offer a glimmer of hope for a future where our digital lives can be both connected and secure. It’s a journey that requires collaboration between individuals, businesses, and governments, a shared responsibility to safeguard our digital freedoms.
