The Future of Blockchain in Improving Digital Privacy Standards is more than just a tech buzzword; it’s a potential revolution. Imagine a world where your data is truly yours, secured not by a corporation, but by the unbreakable chain of a decentralized system. This isn’t science fiction – blockchain’s inherent security features, like cryptographic hashing and consensus mechanisms, are already transforming how we think about digital privacy. This exploration dives into the potential, the challenges, and the ethical considerations of this groundbreaking technology.
From secure data storage and identity management to mitigating data breaches, blockchain offers a compelling alternative to traditional, centralized systems. We’ll unpack the intricacies of how it works, explore real-world applications, and address the inevitable hurdles, like scalability and potential vulnerabilities. Get ready to unpack the future of online privacy – one block at a time.
Blockchain Technology Fundamentals and Privacy
Source: ctomagazine.com
Blockchain’s potential to revolutionize digital privacy is huge, offering secure, transparent data management. This is especially crucial in sectors like healthcare, where sensitive patient information needs airtight protection. Think about how this intersects with the advancements in AI, as detailed in this insightful article on The Role of AI in Streamlining Healthcare Operations and Patient Care , where AI’s efficiency gains can be further bolstered by blockchain’s inherent security.
Ultimately, a combined approach promises a future where both privacy and efficiency thrive.
Blockchain technology is revolutionizing how we think about data security and privacy. Its core strength lies in its ability to create a transparent, yet secure, system that empowers individuals with more control over their digital lives. This is a significant departure from traditional centralized systems where a single entity holds all the power.
Decentralization and Immutability
At its heart, a blockchain is a distributed, shared ledger. This means that instead of being stored in a single location, the data is replicated across a network of computers. This decentralization makes it incredibly difficult for any single entity to manipulate or control the data. Furthermore, the immutable nature of blockchain means that once data is recorded, it cannot be altered or deleted. Each block of data is cryptographically linked to the previous one, creating an unbroken chain. This makes tampering instantly detectable. Think of it like a digital, tamper-proof record book that everyone can see but no one can erase or rewrite.
Cryptographic Hashing and Consensus Mechanisms
Blockchain’s security hinges on cryptographic hashing and consensus mechanisms. Cryptographic hashing transforms data into a unique, fixed-length string of characters (the “hash”). Even a tiny change to the original data results in a completely different hash. This ensures data integrity. Consensus mechanisms, on the other hand, are the rules that govern how new blocks of data are added to the chain. Different mechanisms (like Proof-of-Work or Proof-of-Stake) achieve this consensus in different ways, each impacting the level of security and energy efficiency. The combination of hashing and consensus creates a robust and secure system that prevents unauthorized modifications.
Blockchain vs. Centralized Databases: A Privacy Comparison
Traditional centralized databases, such as those used by many companies, are vulnerable to single points of failure and data breaches. A hacker gaining access to a central server can compromise all the data stored there. Blockchain, however, distributes the data, making it much harder to compromise the entire system. While centralized databases typically rely on the database administrator for access control, blockchain offers more granular control to individuals, allowing them to choose who can access their data. However, public blockchains, while transparent, may not offer complete anonymity; depending on the implementation, transactions can still be linked to identities. Private blockchains, on the other hand, can offer greater privacy by controlling access to the network.
Comparison of Blockchain Consensus Mechanisms and Their Impact on Privacy
The choice of consensus mechanism significantly impacts the privacy and security of a blockchain network. Here’s a comparison:
| Consensus Mechanism | Description | Privacy Implications | Energy Consumption |
|---|---|---|---|
| Proof-of-Work (PoW) | Requires miners to solve complex computational problems to validate transactions. | Relatively low privacy due to public transaction history. | High |
| Proof-of-Stake (PoS) | Validators are chosen based on the amount of cryptocurrency they hold. | Can offer improved privacy through techniques like sharding and zero-knowledge proofs. | Lower than PoW |
| Practical Byzantine Fault Tolerance (PBFT) | Uses a smaller, pre-selected set of validators. | Potentially higher privacy due to limited network participation, but susceptible to collusion. | Low |
| Delegated Proof-of-Stake (DPoS) | Users vote for delegates who validate transactions. | Privacy level varies depending on the implementation and the delegates’ actions. | Low |
Blockchain’s Role in Enhancing Data Privacy: The Future Of Blockchain In Improving Digital Privacy Standards
Blockchain technology, with its decentralized and immutable nature, offers a compelling solution to many of the privacy challenges inherent in our increasingly digital world. Its inherent security features and transparent transaction history can revolutionize how we handle sensitive information, shifting control back to individuals and strengthening defenses against data breaches. This isn’t just theoretical; real-world applications are already demonstrating blockchain’s power to enhance data privacy.
Blockchain improves digital privacy through several key mechanisms. Its decentralized structure eliminates single points of failure, making it significantly more resilient to attacks than traditional centralized systems. Furthermore, cryptographic hashing and encryption techniques ensure data integrity and confidentiality, protecting sensitive information from unauthorized access.
Secure Data Storage and Identity Management
Blockchain offers a secure and transparent method for storing data. Instead of relying on a single entity to control and manage data, blockchain distributes it across a network of nodes. This makes it incredibly difficult for malicious actors to alter or delete data, ensuring its integrity. In identity management, blockchain can create self-sovereign digital identities, empowering individuals to control their own data and share it selectively with others. Imagine a system where you, and only you, hold the keys to your digital identity, deciding which organizations can access specific pieces of information. This contrasts sharply with current systems where companies often hoard vast amounts of personal data with little transparency or user control.
Facilitating Secure Data Sharing with User Control and Anonymity
Blockchain enables secure data sharing while maintaining user control and anonymity through the use of techniques like zero-knowledge proofs and homomorphic encryption. Zero-knowledge proofs allow users to prove the validity of certain information without revealing the information itself. For example, a user could prove they are over 18 years old without disclosing their exact age. Homomorphic encryption allows computations to be performed on encrypted data without decryption, preserving privacy during processing. This technology enables secure data sharing in various applications, from healthcare to finance, where confidentiality is paramount.
Mitigating Data Breaches and Unauthorized Access
The decentralized and immutable nature of blockchain significantly reduces the risk of data breaches. Since data is not stored in a single location, a breach affecting one node doesn’t compromise the entire system. Moreover, the cryptographic hashing and encryption techniques used in blockchain make it extremely difficult for unauthorized individuals to access or modify data. The transparent and auditable nature of blockchain transactions also allows for quick detection and response to any potential security incidents. The inherent traceability of blockchain transactions aids in forensic investigations and accountability.
Hypothetical System: Secure Medical Record Management
Imagine a blockchain-based system for managing medical records. Each patient would possess a unique digital identity on the blockchain, granting them complete control over their medical data. Healthcare providers could access specific records only with the patient’s explicit permission, using cryptographic keys to authenticate access requests. The blockchain would record all access attempts, providing an immutable audit trail for transparency and accountability. This system could significantly improve patient privacy, reduce the risk of data breaches, and streamline data sharing among healthcare professionals while ensuring compliance with regulations like HIPAA. The system would incorporate advanced encryption techniques to safeguard the confidentiality of sensitive medical information, and access control mechanisms would be based on granular permissions defined by the patient, ensuring only authorized parties can view specific data elements.
Addressing Privacy Challenges in Blockchain Implementations
Blockchain’s inherent transparency, while a strength for trust and accountability, presents a significant hurdle for privacy. The immutable nature of the ledger means that all transactions are potentially visible to everyone. This section delves into the complexities of safeguarding privacy within blockchain systems, exploring existing solutions, scalability issues, potential vulnerabilities, and the crucial trade-off between privacy and transparency.
Privacy-Enhancing Technologies in Blockchain
Several technologies aim to mitigate the privacy risks associated with blockchain. These techniques enhance confidentiality without sacrificing the core functionalities of the blockchain. Effective implementation requires careful consideration of their individual strengths and limitations, often necessitating a hybrid approach.
- Zero-Knowledge Proofs (ZKPs): ZKPs allow one party to prove to another that a statement is true without revealing any information beyond the truth of the statement itself. For instance, a user could prove they own a certain amount of cryptocurrency without revealing their exact balance or transaction history. ZKPs are being actively integrated into various blockchain platforms, improving privacy without compromising the system’s security.
- Homomorphic Encryption: This powerful technique enables computations to be performed on encrypted data without requiring decryption. Imagine a scenario where financial institutions need to analyze aggregated transaction data for regulatory compliance without accessing individual user data. Homomorphic encryption makes this possible, enabling secure analysis of encrypted information, maintaining privacy while allowing necessary calculations.
Scalability and Performance Challenges of Privacy-Preserving Solutions
Integrating privacy-enhancing technologies often comes with performance trade-offs. ZKPs and homomorphic encryption, while powerful, can be computationally expensive, potentially slowing down transaction processing and increasing network congestion. The computational overhead associated with these techniques can significantly impact the scalability of blockchain networks, particularly as the number of users and transactions grows. For example, implementing ZKPs on a large-scale public blockchain like Bitcoin would drastically increase the block size and processing time, creating significant bottlenecks. Ongoing research focuses on optimizing these technologies to improve their efficiency and scalability.
Potential Vulnerabilities and Attacks Affecting Blockchain Privacy
Despite advancements in privacy-enhancing technologies, blockchain systems remain susceptible to various attacks that could compromise user privacy. These vulnerabilities highlight the ongoing need for robust security measures and continuous improvements in privacy-preserving techniques.
- Smart Contract Vulnerabilities: Flaws in the code of smart contracts can expose sensitive data. Malicious actors could exploit these vulnerabilities to extract private information, potentially leading to significant privacy breaches.
- Data Leakage through Metadata: Even with encrypted data, metadata associated with transactions (e.g., timestamps, transaction amounts) can reveal sensitive information through careful analysis. Techniques to mitigate this are still under development.
- Side-Channel Attacks: These attacks exploit information leaked through indirect channels, such as power consumption or timing variations, to infer private data. This necessitates robust hardware and software security measures.
The Trade-off Between Privacy and Transparency in Blockchain, The Future of Blockchain in Improving Digital Privacy Standards
The fundamental tension in blockchain design lies in balancing the benefits of transparency with the need for user privacy. Transparency fosters trust and accountability, while privacy protects sensitive user data. This trade-off necessitates careful consideration of the specific use case. For example, a public blockchain designed for financial transactions might prioritize transparency for auditing purposes, while a supply chain management blockchain might prioritize privacy to protect sensitive business information. The optimal balance between these two critical aspects depends heavily on the specific application and its security and privacy requirements. Finding the right equilibrium often involves employing a combination of privacy-enhancing techniques and carefully designed blockchain architectures.
Future Trends and Developments in Blockchain Privacy
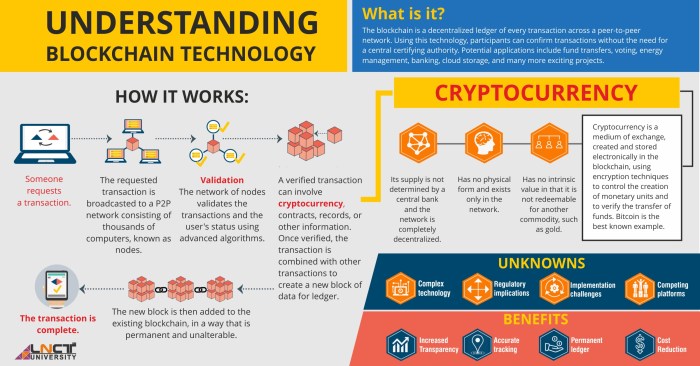
Source: ac.in
The quest for enhanced privacy in the blockchain space is a dynamic field, constantly evolving with new research and technological advancements. While blockchain’s inherent transparency is a strength, it also presents privacy challenges. Overcoming these hurdles is crucial for wider adoption and trust. This section explores emerging trends and developments aiming to bridge this gap.
Significant efforts are underway to bolster blockchain privacy. These efforts range from improving existing cryptographic techniques to developing entirely new privacy-enhancing protocols. The goal is to allow for secure and verifiable transactions without revealing sensitive user information. This involves a complex interplay of cryptography, consensus mechanisms, and smart contract design.
Decentralized Identity Management and its Impact on User Privacy
Decentralized identity (DID) management is poised to revolutionize how we manage and control our digital identities. Instead of relying on centralized authorities like social media platforms or governments, DID systems empower individuals to own and manage their identity data on a blockchain. This means users can selectively share only the necessary information with specific entities, significantly reducing the risk of data breaches and misuse. For example, imagine applying for a loan: you could provide only your credit score and relevant financial information without revealing your full name, address, or other sensitive personal data. This level of granular control offers unprecedented privacy benefits.
Privacy on Public vs. Private Blockchains
Public and private blockchains adopt different approaches to achieving privacy. Public blockchains, like Bitcoin, prioritize transparency, making all transactions publicly viewable. However, techniques like zero-knowledge proofs and ring signatures can enhance privacy on public blockchains by obscuring the identities of participants while maintaining transaction verifiability. In contrast, private blockchains, by their nature, restrict access to authorized participants only. This inherent limitation enhances privacy but compromises the decentralized nature of blockchain technology. Permissioned blockchains, a middle ground, offer a balance by allowing selective access to the network while retaining a degree of transparency. The choice between public and private approaches depends heavily on the specific application and its privacy requirements.
Projected Evolution of Blockchain Privacy Technologies (2024-2034)
The next decade will likely witness significant advancements in blockchain privacy. We can envision a timeline like this:
By 2026-2028: Widespread adoption of privacy-enhancing techniques like zero-knowledge proofs and homomorphic encryption will become commonplace in many blockchain applications. We’ll see more sophisticated smart contracts designed to handle sensitive data securely. This period will also witness the maturation of decentralized identity solutions, with increased integration into various online services.
By 2029-2032: The emergence of quantum-resistant cryptographic algorithms will be crucial, addressing the potential threat of quantum computers to existing encryption methods. This will ensure the long-term security and privacy of blockchain systems. Furthermore, more robust regulatory frameworks surrounding blockchain privacy will likely emerge, leading to standardized privacy protocols and best practices.
By 2033-2034: We can anticipate the development of fully privacy-preserving blockchain systems, capable of handling sensitive data without compromising verifiability. This may involve integrating advanced cryptographic techniques with novel consensus mechanisms to create a truly private and secure decentralized ecosystem. The integration of blockchain technology with other privacy-enhancing technologies, such as differential privacy, will also become more prevalent, leading to enhanced data protection.
Regulatory and Ethical Considerations
Source: lcx.com
Blockchain technology’s potential to revolutionize digital privacy is undeniable, but its implementation isn’t without its hurdles. Navigating the complex landscape of legal frameworks and ethical dilemmas is crucial for realizing blockchain’s privacy-enhancing capabilities responsibly. This section explores the regulatory and ethical considerations that shape the future of privacy-focused blockchain applications.
The intersection of blockchain and privacy is a rapidly evolving field, attracting both excitement and scrutiny. Existing data protection laws, coupled with emerging regulations specifically targeting blockchain, are shaping how developers and organizations approach privacy-enhancing blockchain technologies. Ethical concerns around data ownership, surveillance capabilities, and the potential for algorithmic bias add another layer of complexity to the equation.
Current and Emerging Legal Frameworks
Several legal frameworks are already impacting or will soon significantly influence the development and use of privacy-enhancing blockchain technologies. Existing data protection regulations like GDPR in Europe and CCPA in California provide a foundation, requiring transparency and user consent regarding data collection and processing. However, the decentralized and pseudonymous nature of blockchain presents unique challenges to these frameworks. New regulations are emerging specifically addressing cryptocurrencies and blockchain technologies, aiming to balance innovation with consumer protection and preventing illicit activities. For example, the Travel Rule, implemented by the Financial Action Task Force (FATF), necessitates the identification of parties involved in cryptocurrency transactions above certain thresholds, potentially impacting the anonymity provided by some blockchain solutions. The interplay between these existing and emerging regulations requires careful navigation to ensure compliance while preserving the privacy-enhancing benefits of blockchain.
Ethical Implications of Blockchain for Data Privacy
The ethical implications of using blockchain for data privacy are multifaceted and require careful consideration. While blockchain offers the potential for enhanced data security and control, it also raises concerns about data ownership, surveillance, and bias. The question of who truly owns the data stored on a blockchain, especially in decentralized systems, needs careful examination. The immutability of blockchain data can create challenges for data correction or deletion, potentially leading to the perpetuation of inaccuracies or harmful information. Furthermore, the potential for blockchain-based surveillance systems, tracking individual activities and creating detailed profiles, raises significant ethical concerns about privacy infringement. Algorithmic bias embedded in smart contracts or decentralized applications built on blockchain can perpetuate and amplify existing societal inequalities. Addressing these ethical concerns requires a proactive and responsible approach to development and deployment.
Best Practices for Ethical and Responsible Implementation
To ensure ethical and responsible implementation of blockchain for privacy purposes, developers and organizations should adopt several best practices. These include:
- Prioritizing user privacy by design, embedding privacy considerations into every stage of development.
- Implementing robust data minimization and anonymization techniques to reduce the amount of personal data stored on the blockchain.
- Ensuring transparency and user control over data, allowing users to access, modify, and delete their data as needed.
- Conducting thorough privacy impact assessments to identify and mitigate potential risks.
- Adhering to relevant data protection laws and regulations.
- Promoting open source development and community audits to foster transparency and accountability.
- Establishing clear data governance frameworks and procedures.
Potential Misuse and Risk Mitigation Strategies
Despite its potential benefits, blockchain technology is not immune to misuse. Potential scenarios include the creation of illicit marketplaces for illegal goods and services, the facilitation of money laundering and terrorist financing, and the development of sophisticated surveillance systems. Mitigating these risks requires a multi-pronged approach involving technological solutions, regulatory frameworks, and public awareness campaigns. Technological solutions could include enhanced transaction monitoring, improved cryptographic techniques, and the development of privacy-preserving protocols. Strong regulatory frameworks, coupled with international cooperation, are essential to curb the misuse of blockchain for illicit activities. Public awareness campaigns can educate users about the risks and benefits of blockchain technology, promoting responsible usage and empowering them to make informed decisions.
Closure
Ultimately, the future of digital privacy hinges on embracing innovative solutions like blockchain. While challenges remain – from scalability issues to regulatory hurdles – the potential benefits are undeniable. By carefully navigating the ethical considerations and addressing potential vulnerabilities, we can harness the power of blockchain to create a more secure and private digital landscape. The journey towards truly secure digital identities and data is underway, and blockchain is leading the charge.
