How Blockchain is Creating Decentralized Systems for Digital Security: Forget passwords, forget single points of failure. We’re diving deep into the revolutionary world of blockchain, exploring how this tech is reshaping digital security by distributing power and making our data virtually unhackable. Think of it as a digital fortress, built not by one entity but by a network of computers, each verifying the others. It’s a game-changer, and we’re breaking down exactly how it works.
From understanding the core principles of decentralized systems to exploring the nitty-gritty of blockchain technology – including its various consensus mechanisms like Proof-of-Work and Proof-of-Stake – we’ll unpack how this tech protects our data, from individual identities to massive supply chains. We’ll also look at the exciting applications of decentralized apps (dApps) and how cryptography forms the backbone of this secure ecosystem. Get ready to unlock the secrets of a more secure digital future.
Introduction to Decentralized Systems and Digital Security: How Blockchain Is Creating Decentralized Systems For Digital Security
Decentralized systems are shaking up the digital world, offering a fresh approach to security that contrasts sharply with traditional, centralized models. Instead of relying on a single point of control, they distribute power and responsibility across a network of participants. This fundamental shift has significant implications for how we think about and manage digital security.
Centralized systems, on the other hand, present a tempting target for hackers. Their architecture, with all data and control concentrated in one place, creates a single point of failure. A successful breach can compromise the entire system, leading to widespread data loss, financial damage, and reputational harm. This vulnerability is amplified by the increasing reliance on digital infrastructure in almost every aspect of modern life.
Vulnerabilities of Centralized Systems in Digital Security
The inherent weakness of centralized systems lies in their singular point of control. A single compromised server, a rogue administrator, or a successful phishing attack can unravel the entire system. Consider a large social media platform: if its central database is breached, the personal information of millions of users is at risk. This vulnerability extends beyond data breaches to encompass manipulation and censorship. A single entity controlling the platform can alter information, suppress dissent, or even shut down access at will. This lack of transparency and control is a significant security concern.
Real-World Applications of Decentralized Systems Enhancing Security
Decentralized systems offer a compelling alternative by distributing trust and control. Blockchain technology, for example, underpins many of these systems. Its immutable ledger, replicated across numerous nodes, makes it extremely difficult to alter or compromise data. Cryptocurrencies like Bitcoin exemplify this enhanced security. Transactions are verified by a distributed network of miners, making them resistant to fraud and censorship. Furthermore, decentralized storage solutions like IPFS (InterPlanetary File System) offer resilience against data loss and censorship by distributing data across a vast network of nodes. If one node fails, the data remains accessible through other nodes. This contrasts sharply with centralized cloud storage where a single server failure can lead to data inaccessibility. Another example is decentralized identity systems, where individuals control their own digital identities rather than relying on a central authority, reducing the risk of identity theft and data breaches.
Blockchain Technology
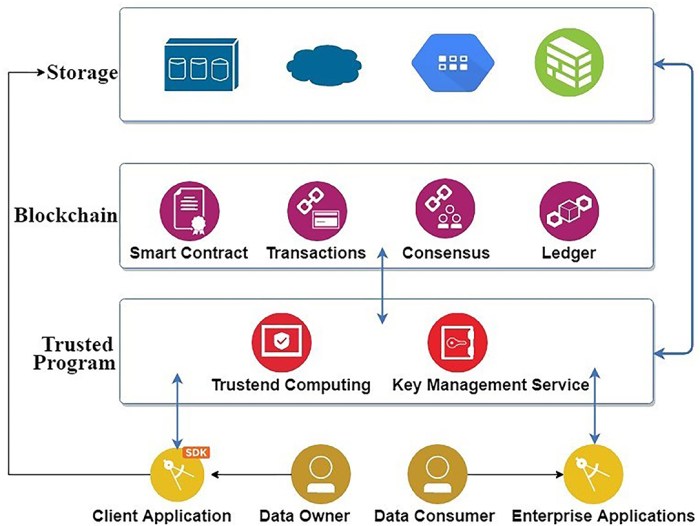
Source: frontiersin.org
Blockchain technology is the backbone of decentralized systems, offering a revolutionary approach to data management and security. Unlike traditional centralized databases controlled by a single entity, blockchain distributes data across a network of computers, making it incredibly resilient and transparent. This decentralized nature is what allows for enhanced security and trust.
At its core, a blockchain is a chain of blocks. Each block contains a set of validated transactions, a timestamp, and a cryptographic hash that links it to the previous block. This chain-like structure creates an immutable record of all transactions, making it virtually impossible to alter or delete data without detection.
Blockchain’s decentralized nature is revolutionizing digital security, offering trustless systems for data management. This is especially crucial as we build smarter cities, leveraging the interconnectedness of the Internet of Things (IoT) as described in this insightful article: The Role of IoT in Building Smarter Cities. Ultimately, secure IoT infrastructure relies heavily on robust, blockchain-powered security to protect the sensitive data driving these urban innovations.
Blockchain Components
The fundamental components of blockchain technology are blocks, the chain itself, and the consensus mechanism. Blocks are the containers for transactions, acting like individual pages in a ledger. The chain links these blocks chronologically, forming a continuous and verifiable record. The consensus mechanism is the crucial element that governs how new blocks are added to the chain, ensuring the integrity and security of the network.
Immutability and Enhanced Digital Security, How Blockchain is Creating Decentralized Systems for Digital Security
Blockchain’s immutability is its most powerful security feature. Because each block is cryptographically linked to the previous one, any attempt to alter a past transaction would require altering all subsequent blocks. This is computationally infeasible due to the cryptographic hashing and the distributed nature of the blockchain. This high level of security makes blockchain ideal for applications requiring high levels of trust and transparency, such as supply chain management, digital identity verification, and secure voting systems. For example, imagine tracking a pharmaceutical product’s journey from manufacturer to consumer. A blockchain record would make it impossible to forge or tamper with information about its origin, handling, and storage.
Consensus Mechanisms
Several consensus mechanisms exist, each with its strengths and weaknesses. The choice of mechanism significantly impacts the blockchain’s performance, security, and scalability. Two prominent examples are Proof-of-Work (PoW) and Proof-of-Stake (PoS).
Proof-of-Work, famously used by Bitcoin, requires miners to solve complex computational puzzles to validate transactions and add new blocks. This process consumes significant energy but provides a high level of security due to the computational barrier to entry for malicious actors. Proof-of-Stake, on the other hand, selects validators based on the amount of cryptocurrency they stake. This is generally considered more energy-efficient than PoW. Other mechanisms, like Delegated Proof-of-Stake (DPoS) and Practical Byzantine Fault Tolerance (PBFT), offer alternative approaches with varying trade-offs between security, efficiency, and scalability.
Comparison of Consensus Mechanisms
| Consensus Mechanism | Advantages | Disadvantages | Example |
|---|---|---|---|
| Proof-of-Work (PoW) | High security, decentralized, resistant to 51% attacks (with sufficient hash power) | High energy consumption, slow transaction speeds, scalability challenges | Bitcoin |
| Proof-of-Stake (PoS) | Energy efficient, faster transaction speeds, potentially higher scalability | Vulnerable to “nothing-at-stake” attacks (though mitigated by various techniques), potential for centralization if a few large stakeholders control a majority of the stake | Ethereum (after the merge) |
| Delegated Proof-of-Stake (DPoS) | Fast transaction speeds, relatively high scalability | Potential for centralization, vulnerability to attacks if a significant number of delegates are compromised | EOS |
| Practical Byzantine Fault Tolerance (PBFT) | High fault tolerance, fast transaction speeds in smaller networks | Scalability limitations, not suitable for large, public networks | Hyperledger Fabric (a permissioned blockchain) |
Blockchain’s Role in Secure Data Management
Blockchain technology, with its inherent immutability and transparency, is revolutionizing how we manage and secure digital data. Its decentralized nature offers a powerful alternative to traditional centralized systems, addressing concerns about data breaches, single points of failure, and lack of trust. This section explores how blockchain enhances data security and management across various sectors.
Blockchain-Based Secure Digital Identities
Blockchain facilitates the creation of secure and verifiable digital identities. Instead of relying on centralized authorities, individuals can control and manage their own digital identities on a blockchain. This self-sovereign identity approach allows individuals to selectively share their data with different entities, enhancing privacy and control. For instance, a user might use a blockchain-based identity to prove their age to access a service without revealing other personal information. The immutability of the blockchain ensures that identity records are tamper-proof and readily auditable, providing a high level of trust and security.
Blockchain’s Facilitation of Secure Data Storage and Access Control
Blockchain technology enables secure data storage through cryptographic hashing and distributed ledger technology. Data isn’t stored directly on the blockchain but rather, a cryptographic hash representing the data is stored. This hash acts as a fingerprint, uniquely identifying the data. Access control is managed through smart contracts, which define rules for who can access and modify the data. This approach eliminates the need for a central authority to control access, ensuring data privacy and reducing the risk of unauthorized access. Furthermore, the distributed nature of the blockchain means that data is not stored in a single location, making it more resilient to attacks and data loss.
Examples of Blockchain Applications in Data Management
Blockchain’s impact on data management is evident across numerous industries. In supply chain management, blockchain provides complete transparency and traceability of goods, from origin to consumer. Each transaction, including location, time, and handling, is recorded on the blockchain, making it easy to identify and prevent counterfeiting or fraud. In healthcare, blockchain can be used to securely store and manage patient medical records, ensuring data privacy and facilitating interoperability between healthcare providers. Patients have more control over their data, and authorized personnel can access the necessary information securely and efficiently. Other applications include secure voting systems, intellectual property management, and digital asset management.
Hypothetical Scenario: Improving Data Integrity in the Pharmaceutical Industry
Imagine a pharmaceutical company using blockchain to track the entire lifecycle of a drug, from manufacturing to distribution. Each stage, including raw material sourcing, manufacturing processes, quality control checks, and distribution channels, is recorded on a shared, immutable blockchain. This provides complete transparency and traceability, allowing for immediate identification of any discrepancies or potential issues. If a batch of drugs is found to be contaminated, the blockchain allows for quick identification of the affected batches and their distribution path, enabling a swift and effective recall, minimizing potential harm and protecting public health. This scenario demonstrates how blockchain enhances data integrity and accountability within the pharmaceutical industry, significantly improving patient safety and trust.
Decentralized Applications (dApps) and Security
Decentralized applications, or dApps, represent a paradigm shift in software development, leveraging blockchain technology to create applications that are resistant to censorship and single points of failure. Unlike traditional apps reliant on centralized servers, dApps distribute functionality across a network of nodes, enhancing security and resilience. This section explores the unique characteristics of dApps, their security advantages, developmental challenges, and common security threats.
dApps are built on decentralized networks, typically blockchains, and offer a unique set of characteristics that differentiate them from traditional applications. These characteristics directly impact their security posture.
Key Characteristics of Decentralized Applications
Decentralized applications are distinguished by several key features. They are typically open-source, meaning their code is publicly accessible and verifiable, fostering transparency and community-driven security audits. Their functionality is distributed across multiple nodes, making them resistant to single points of failure and censorship. Furthermore, dApps often utilize cryptographic techniques to ensure data integrity and user authentication, enhancing security. Finally, they often employ tokenized economies, using cryptocurrencies to incentivize participation and governance within the dApp ecosystem.
Security Advantages of dApps Compared to Traditional Applications
The decentralized nature of dApps offers significant security advantages over traditional applications. Because data isn’t stored in a single location, the risk of a single point of compromise is greatly reduced. A successful attack on one node does not compromise the entire system. Furthermore, the transparency inherent in open-source dApps allows for community-driven security audits, identifying vulnerabilities before they can be exploited. The use of cryptography enhances data integrity and authenticity, protecting against unauthorized modifications and ensuring data provenance.
Challenges in Developing and Securing dApps
Despite the inherent security benefits, developing and securing dApps presents unique challenges. The complexity of decentralized systems necessitates specialized expertise in blockchain technology, cryptography, and distributed systems. Ensuring interoperability between different blockchains and dApps is also a significant hurdle. Furthermore, the open-source nature, while beneficial for transparency, also exposes the code to potential attackers who can scrutinize it for vulnerabilities. Finally, the decentralized nature can make debugging and troubleshooting significantly more difficult than in centralized systems.
Common Security Threats Faced by dApps and Mitigation Strategies
dApps, while offering enhanced security, are still vulnerable to various attacks. Understanding these threats and implementing appropriate mitigation strategies is crucial for building secure and robust dApps.
- Smart Contract Vulnerabilities: Bugs in smart contracts can lead to significant financial losses and system compromises. Mitigation involves rigorous code auditing, formal verification techniques, and using established security best practices during development.
- Oracle Manipulation: dApps often rely on oracles to fetch external data. Manipulating this data can lead to incorrect application behavior and security breaches. Mitigation involves using multiple, trusted oracles and implementing mechanisms to verify the accuracy of the data received.
- Denial-of-Service (DoS) Attacks: Overwhelming the network with requests can render a dApp unavailable. Mitigation involves implementing robust network infrastructure, employing rate-limiting techniques, and using distributed consensus mechanisms that are resistant to DoS attacks.
- Sybil Attacks: Creating multiple fake identities to gain undue influence or control within the dApp’s network. Mitigation involves using reputation systems, identity verification mechanisms, and robust consensus algorithms to prevent malicious actors from gaining disproportionate influence.
- Phishing and Social Engineering: Tricking users into revealing their private keys or sensitive information. Mitigation involves user education, implementing strong authentication mechanisms, and using secure key management practices.
Blockchain and Cryptography
Blockchain technology wouldn’t be nearly as secure without the robust underpinnings of cryptography. It’s the cryptographic algorithms that ensure the integrity and immutability of the data stored on the blockchain, preventing tampering and fraud. Think of cryptography as the unbreakable lock protecting the valuable information within the blockchain’s digital vault.
Cryptography plays a vital role in securing blockchain transactions by employing various techniques to ensure confidentiality, integrity, and authenticity. These techniques work in concert to create a system where transactions are verifiable, tamper-proof, and traceable, making the blockchain a trusted and transparent ledger.
Hashing Algorithms
Hashing is a fundamental cryptographic technique in blockchain. It involves taking an input (a block of data) and transforming it into a fixed-size string of characters, known as a hash. Even a tiny change in the input data will result in a completely different hash. This one-way function is crucial because it allows for verification of data integrity. If the hash of a block is altered, it immediately signals that the block’s data has been tampered with. Common hashing algorithms used in blockchain include SHA-256 and SHA-3. The strength of these algorithms lies in their resistance to collisions (finding two different inputs that produce the same hash), ensuring the uniqueness of each block’s hash. For instance, if a hacker tried to alter a transaction within a block, the resulting hash would be different, instantly revealing the tampering attempt.
Digital Signatures
Digital signatures are another critical cryptographic component. They provide authentication and non-repudiation, proving that a specific user created or authorized a transaction. Using a private key, a user creates a digital signature for a transaction, which can then be verified using their corresponding public key. This prevents forgery and ensures that only the legitimate owner can authorize transactions. This is analogous to signing a physical document with your signature – only you possess the means to create that specific signature, and its authenticity can be verified by anyone who has your signature on file. The use of asymmetric cryptography, with separate public and private keys, is central to this process.
Elliptic Curve Cryptography (ECC)
Elliptic curve cryptography is a type of public-key cryptography that’s increasingly popular in blockchain systems due to its efficiency and security. ECC uses elliptic curves to generate cryptographic keys, offering comparable security to RSA with significantly shorter key lengths. This is particularly beneficial for resource-constrained devices and networks, making it suitable for various blockchain applications. Bitcoin, for example, uses ECC for its digital signatures. The smaller key sizes contribute to faster transaction processing and reduced storage requirements. The security of ECC relies on the mathematical difficulty of solving the elliptic curve discrete logarithm problem.
Security Implications of Different Cryptographic Algorithms
The choice of cryptographic algorithms significantly impacts the security of a blockchain. Using outdated or weak algorithms can leave the system vulnerable to attacks. For example, using a hashing algorithm susceptible to collisions could allow attackers to manipulate the blockchain. Similarly, weak digital signature algorithms could be broken, enabling unauthorized transactions. The ongoing research and development in cryptography constantly evaluate and improve the algorithms used, ensuring the blockchain’s long-term security. Regular audits and updates of cryptographic implementations are crucial to maintaining the integrity and trustworthiness of blockchain systems. The adoption of newer, more robust algorithms is a continuous process driven by the need to stay ahead of potential threats.
Ensuring Data Integrity and Authenticity
Cryptographic principles, including hashing and digital signatures, work together to ensure the integrity and authenticity of data on a blockchain. The immutability of the blockchain stems directly from the cryptographic properties of the hash chain. Each block’s hash is dependent on the hash of the previous block, creating a chain that is difficult to tamper with. Any alteration to a block would cascade through the chain, making the change instantly detectable. Digital signatures, on the other hand, guarantee the authenticity of transactions by verifying the identity of the sender. This combination of cryptographic techniques creates a highly secure and trustworthy system where data can be reliably stored and accessed. This is fundamentally different from traditional centralized systems where a single point of failure or manipulation can compromise the entire system.
Case Studies
Blockchain technology isn’t just theoretical; it’s actively revolutionizing digital security across various sectors. Let’s dive into some real-world examples demonstrating its impact. These case studies highlight how blockchain’s decentralized and immutable nature addresses critical security vulnerabilities.
Supply Chain Management: Tracking Pharmaceuticals with Blockchain
The pharmaceutical industry faces significant challenges with counterfeit drugs. A blockchain-based solution, implemented by several companies, tracks pharmaceuticals from manufacturing to distribution. Each drug’s journey is recorded on a shared, immutable ledger, making it nearly impossible to tamper with or counterfeit products. This system allows for real-time verification of a drug’s authenticity, enhancing patient safety and reducing the risk of harmful counterfeit medications entering the market. The blockchain solution improves transparency and traceability, creating a secure and reliable record of the product’s journey. This not only prevents counterfeiting but also enables efficient recall management in case of safety issues.
Healthcare Data Management: Secure Patient Record Keeping
Protecting patient health information is paramount. Several healthcare providers are exploring blockchain to enhance the security and privacy of electronic health records (EHRs). By storing patient data on a distributed ledger, blockchain eliminates the single point of failure associated with centralized databases. This decentralization makes the system more resilient to cyberattacks and data breaches. Furthermore, blockchain’s cryptographic techniques ensure data integrity and confidentiality, giving patients greater control over their own medical information. The implementation of blockchain in healthcare improves data security, patient privacy, and interoperability between different healthcare systems.
Digital Identity Management: Verifying Identities Securely
Managing digital identities securely is a growing concern in the digital age. Blockchain technology offers a solution by creating decentralized identity systems. These systems allow individuals to control their own digital identities, providing verifiable credentials without relying on centralized authorities. This approach reduces the risk of identity theft and fraud, while also enhancing user privacy. Blockchain’s cryptographic techniques ensure the authenticity and integrity of digital identities, making them more secure and trustworthy. The decentralized nature of these systems also makes them more resilient to attacks and data breaches.
Key Lessons Learned from These Case Studies
The success of these blockchain implementations highlights several key lessons:
These case studies underscore the transformative potential of blockchain in enhancing digital security. The benefits extend beyond simply preventing breaches; they encompass improved transparency, traceability, and user control over sensitive data.
- Decentralization is Key: Distributing data across multiple nodes significantly reduces vulnerability to single points of failure.
- Immutability Ensures Data Integrity: Once data is recorded on a blockchain, it cannot be altered or deleted, preventing tampering and fraud.
- Transparency Builds Trust: Blockchain’s transparent nature fosters trust among participants, enhancing accountability and security.
- Careful Planning and Implementation are Crucial: Successful blockchain deployments require careful consideration of specific needs and challenges.
Future Trends and Challenges in Blockchain-Based Decentralized Security
The evolution of blockchain technology is rapidly reshaping the landscape of digital security, promising a future where decentralized systems are the norm, not the exception. However, this exciting trajectory is not without its hurdles. Understanding both the emerging trends and inherent limitations is crucial for navigating this technological frontier.
The convergence of blockchain with other cutting-edge technologies is driving innovation in decentralized security. This synergistic effect is leading to more robust and adaptable systems capable of handling the ever-increasing complexity of cyber threats.
Enhanced Privacy and Anonymity Solutions
Blockchain’s inherent transparency can be a double-edged sword. While providing auditability, it can also compromise user privacy. Emerging trends focus on enhancing privacy through techniques like zero-knowledge proofs and homomorphic encryption. These cryptographic methods allow for verification of transactions without revealing sensitive data, creating a more private and secure environment. For instance, Zcash utilizes zero-knowledge proofs to conceal transaction amounts and participant identities while still maintaining the integrity of the blockchain.
Quantum-Resistant Cryptography Integration
The advent of quantum computing poses a significant threat to current cryptographic algorithms. The development and integration of quantum-resistant cryptographic methods into blockchain systems are becoming increasingly vital. Post-quantum cryptography aims to create algorithms resistant to attacks from quantum computers, safeguarding the long-term security of blockchain-based decentralized systems. Projects are already underway to explore and implement these algorithms, ensuring the continued resilience of blockchain technology in the face of future technological advancements.
Improved Scalability and Interoperability
Scalability and interoperability remain key challenges for widespread blockchain adoption. Solutions like sharding (dividing the blockchain into smaller, manageable parts) and layer-2 scaling solutions are improving transaction speeds and reducing congestion. Cross-chain interoperability protocols are also being developed to enable seamless communication and data exchange between different blockchain networks. This enhanced functionality is critical for building truly decentralized and interconnected secure systems. The Cosmos network, for example, is a prominent example of a project focusing on interoperability through its Inter-Blockchain Communication (IBC) protocol.
Challenges and Limitations of Blockchain for Decentralized Security
Despite its potential, blockchain technology faces several challenges in achieving widespread adoption for decentralized security. These obstacles require careful consideration and innovative solutions.
Regulatory Uncertainty and Legal Frameworks
The decentralized nature of blockchain presents unique regulatory challenges. The lack of clear legal frameworks surrounding blockchain technology and its applications creates uncertainty for businesses and developers, hindering broader adoption. Governments worldwide are grappling with how to regulate this emerging technology, and the lack of consistent regulatory environments poses a significant obstacle.
High Energy Consumption and Environmental Concerns
Certain blockchain networks, particularly those using Proof-of-Work consensus mechanisms like Bitcoin, consume significant amounts of energy. This high energy consumption raises environmental concerns and necessitates the exploration of more energy-efficient consensus mechanisms, such as Proof-of-Stake, which are gaining traction for their lower energy footprint.
Complexity and Technical Expertise
Developing and implementing secure blockchain-based systems requires specialized technical expertise. The complexity of blockchain technology can be a barrier to entry for smaller organizations and individuals, limiting its accessibility and potential impact. Furthermore, the lack of skilled developers familiar with blockchain security best practices poses a challenge to the widespread deployment of secure decentralized systems.
Predictions on the Future Role of Blockchain in Creating More Secure Digital Systems
Blockchain technology is poised to play a transformative role in enhancing digital security in the coming years.
Increased Adoption in Various Sectors
We can expect to see increased adoption of blockchain-based security solutions across various sectors, including finance, healthcare, supply chain management, and voting systems. The inherent security and transparency of blockchain will drive its integration into critical infrastructure, improving data integrity and trust. Examples include supply chain tracking using blockchain to prevent counterfeiting and secure voting systems that enhance election integrity.
Hybrid Approaches Combining Blockchain and Traditional Security Measures
A likely trend is the emergence of hybrid approaches, combining the strengths of blockchain technology with traditional security measures. This integrated approach will leverage the best aspects of both worlds, creating more robust and comprehensive security systems. For example, a system might use blockchain for secure data storage while relying on traditional firewalls and intrusion detection systems for perimeter security.
Focus on User-Friendly Interfaces and Improved Accessibility
As blockchain technology matures, there will be a greater focus on creating user-friendly interfaces and improving accessibility for non-technical users. This will make blockchain-based security solutions more readily available and easier to implement, broadening their adoption and impact. This includes the development of intuitive tools and platforms that simplify the complexities of blockchain technology for the average user.
Final Wrap-Up
So, there you have it – a glimpse into the revolutionary world of blockchain-powered decentralized security. While challenges remain, the potential for a more secure and resilient digital landscape is undeniable. Blockchain isn’t just a buzzword; it’s a fundamental shift in how we protect our data and build trust in the digital realm. It’s a future where data breaches become less likely, where control is distributed, and where security isn’t just a feature, but a fundamental design principle. Ready to embrace the decentralized revolution?
